Analysis Report
The analysis report contains all the results on a file that has been submitted for analysis. The report is divided into three sections: Overview, Binary Intelligence and Behavior.
Overview
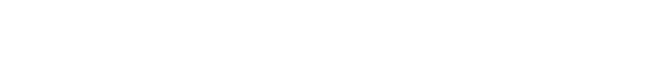
The overview section summarises the results of the Threatray analysis. It aggregates all kinds of findings, such as detection and identification verdicts, as well as intelligence.
- Verdict: This is the verdict of the analysis. The verdict can be ‘unknown’, ‘suspicious’ or ‘malicious’. This is explained in detail here.
- Malware families: An optional list of malware families that were identified.
- Detection: The details of how the detection came to be. Threatray employs various techniques to detect and identify. These are:
- Code: Verdict from Threatray’s code detections. This is explained in detail here.
- AV: Verdict from an OEM antivirus engine.
- YARA: Verdict from YARA rules curated by Threatray.
- Behavior: Verdict based on behavioral detection rules curated by Threatray.
- Intelligence: Any intelligence related to this analysis. This encompasses unvetted community YARA rules. Intelligence does not affect the verdict and is purely informational.
- File metadata: SHA256 hash, filename, type, size and first seen date.
- Analysis metadata: Unique Analysis ID, creation timestamps and analysis type details.
- Actions: Download file, Reanalyse file, Report a false negative or false positive, Delete the analysis.
Binary Intelligence
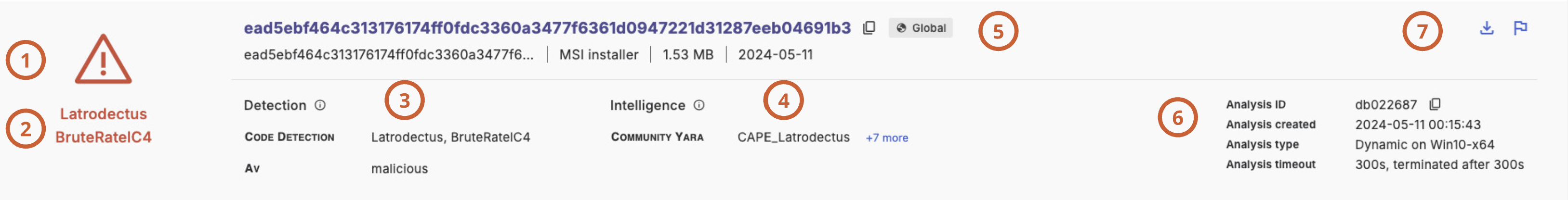
The binary intelligence section gives an overview of all binary code that was extracted and analyzed.
It contains the analysis for the submitted file (1) and the analysis of all memory regions that contain binary code (2). A memory region has either been extracted through dynamic analysis, or extracted statically in case the analysis is from a minidump or an endpoint scan.
Details on Binary Code
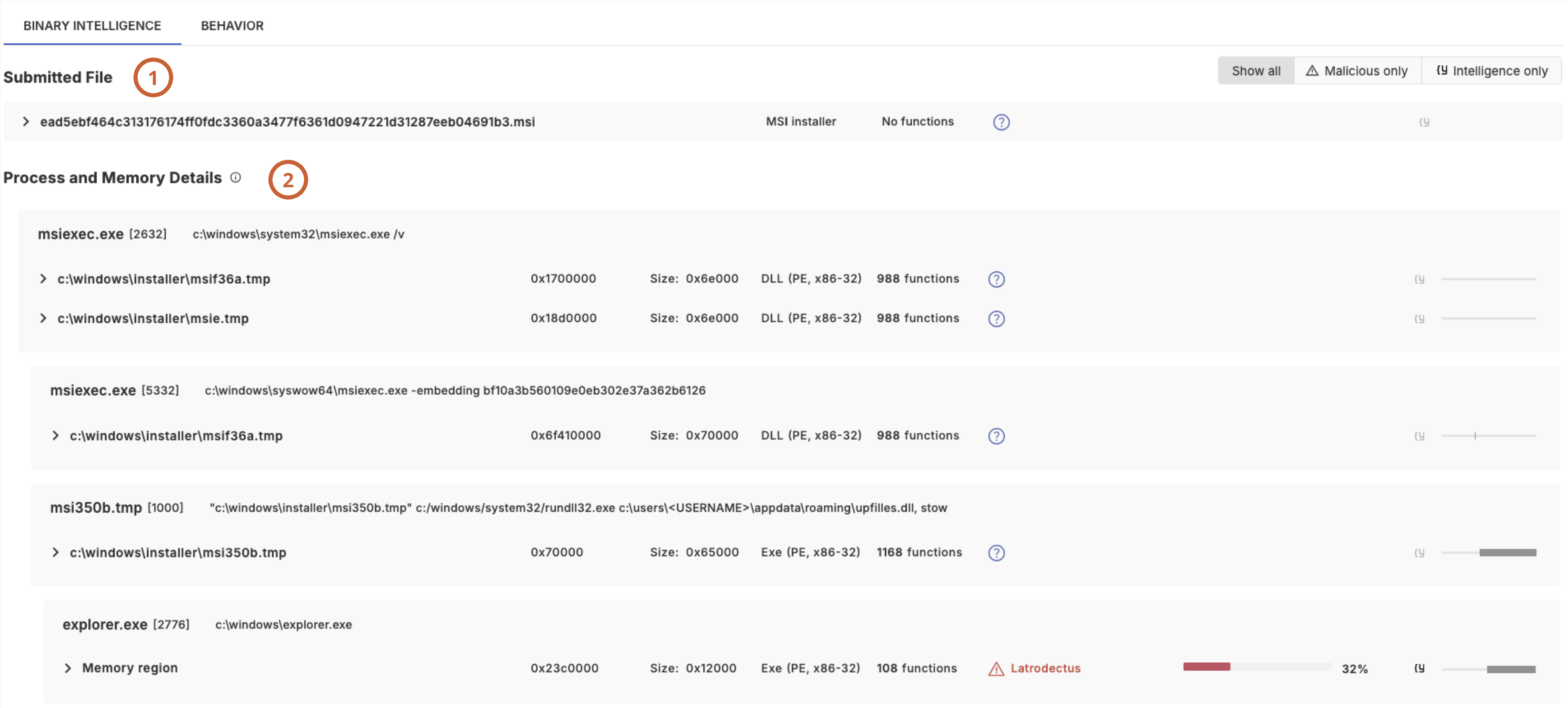
Threatray provides details on the submitted file and each memory region that was analyzed.
In this example, we are looking at the details of a memory region, extracted from the explorer.exe process and identified as Latrodectus. There are several tabs: verdict details, code intelligence, functions, OSINT hunt, capabilities, file information and strings.
Verdict Details
The verdict details tab explains how the verdict came to be. The structure and semantics is the same as in the summary section.
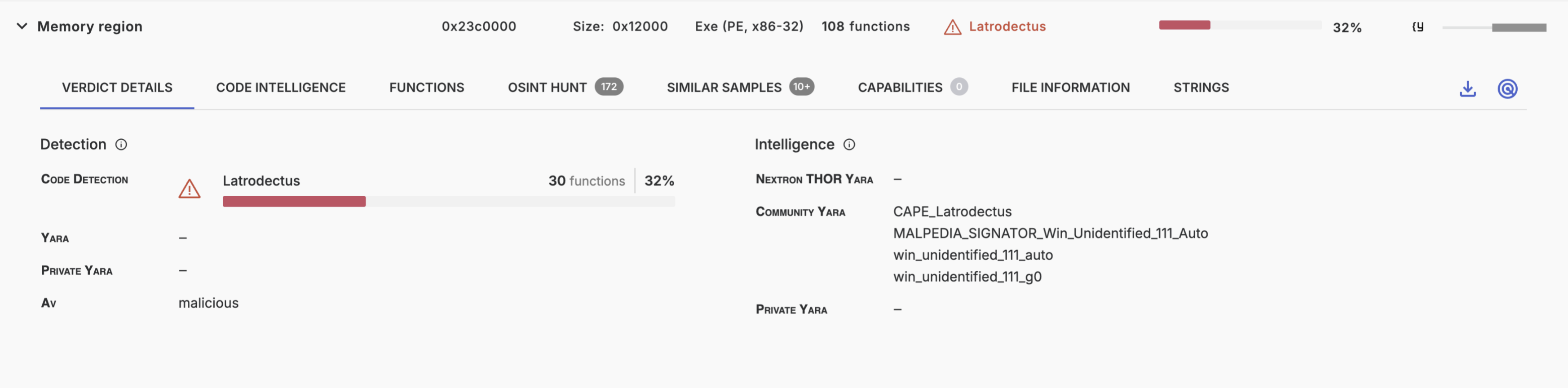
The right-hand side includes the actions: Download the file, Retrohunt for this code.
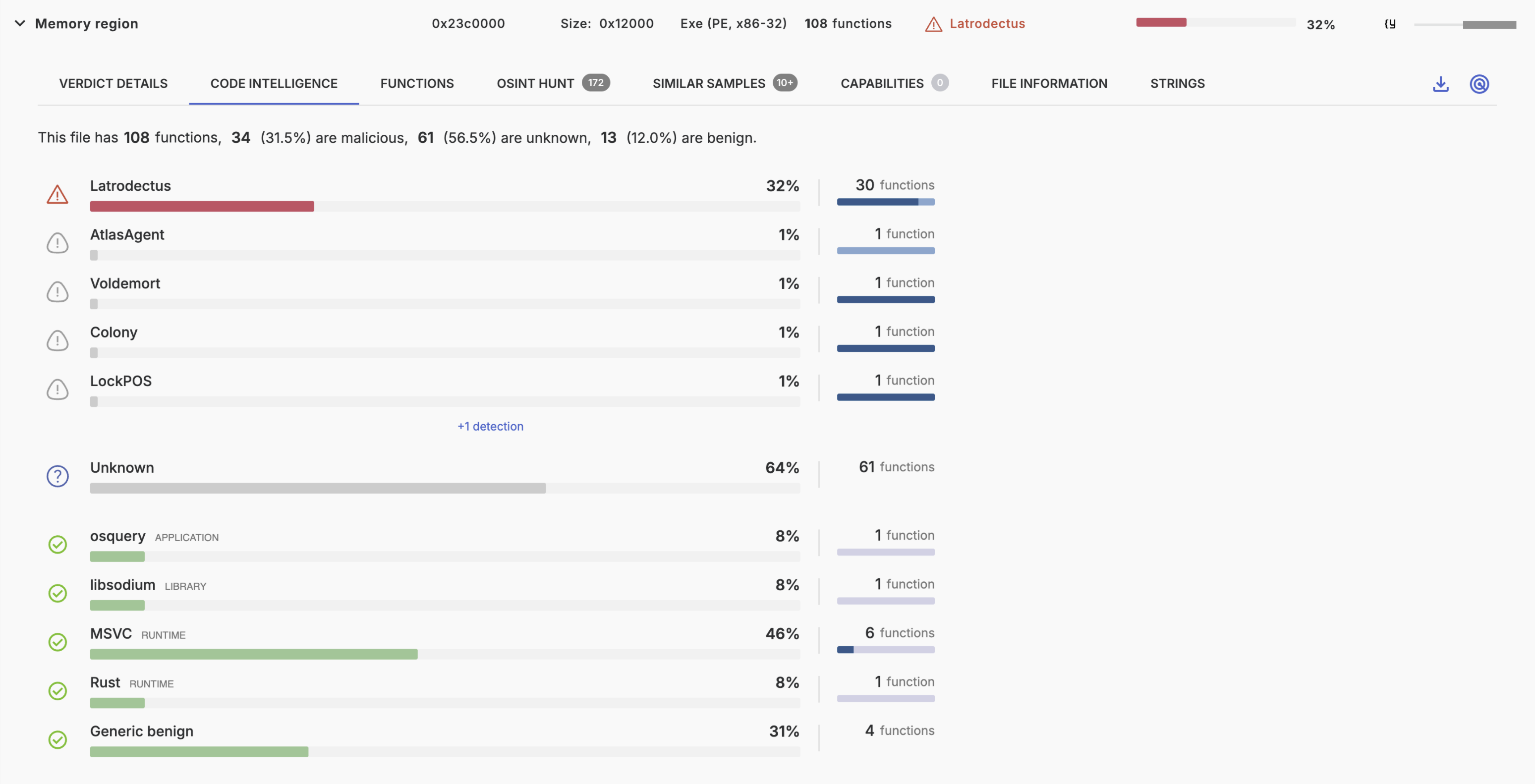
Code Intelligence
Code Intelligence gives a breakdown of the code in this binary file, separated into known bad and known good code. At a certain threshold, these overlaps lead to a suspicious or malicious detection, which we call code detections. This is explained in more detail here .
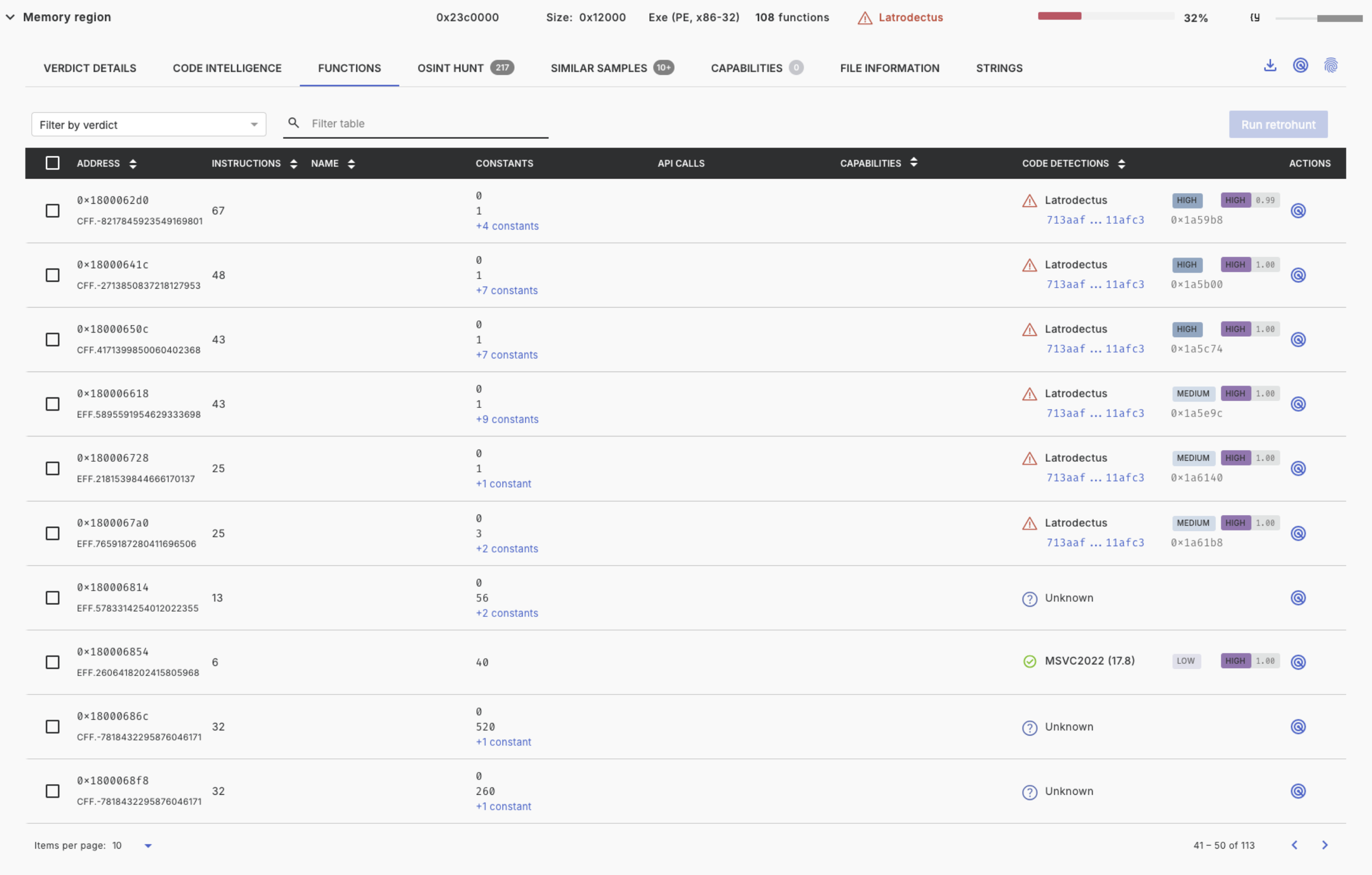
Functions
The functions tab lists all functions of this binary, including disassembly metadata, capabilities associated with a specific function and code detections per function. Each match to a code detection carries a confidence and score, indicating how reliable the match is.
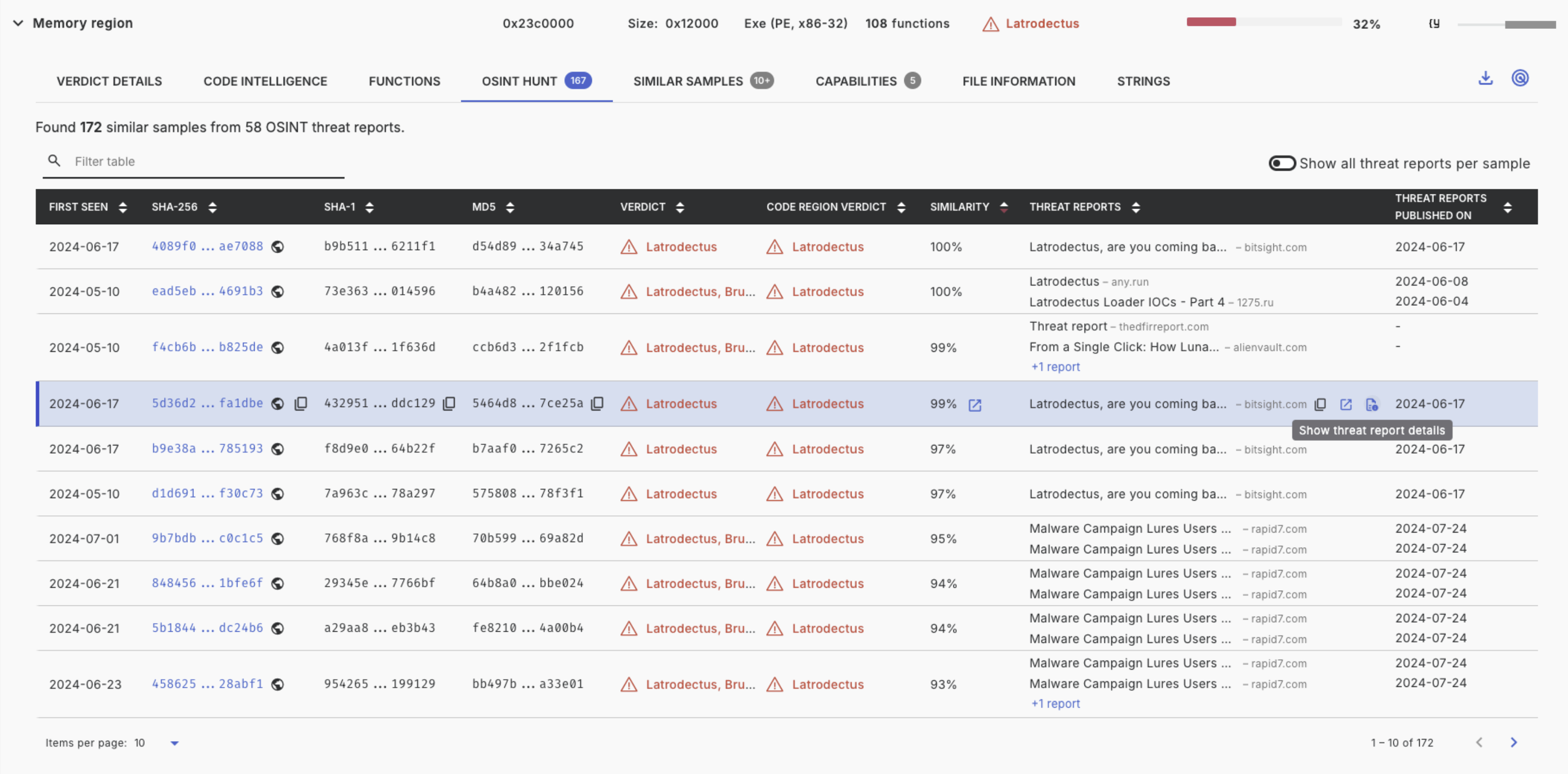
OSINT Hunt
The OSINT Hunt tab shows a list of similar samples that contain this or similar binary code, and were mentioned in Open Source Intelligence (OSINT) threat reports.
Each threat report can be opened, showing a summary of the report and the list of similar samples in this report.
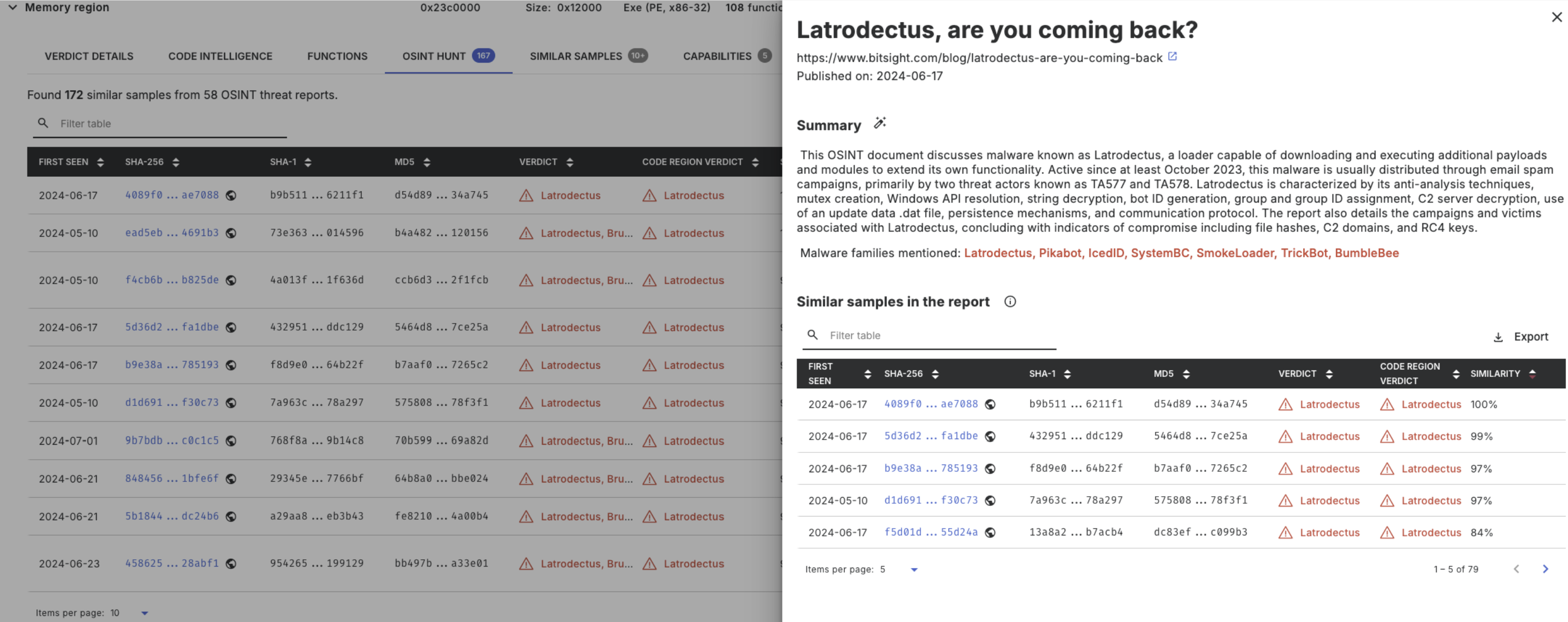
More details on OSINT Hunts can be found here.
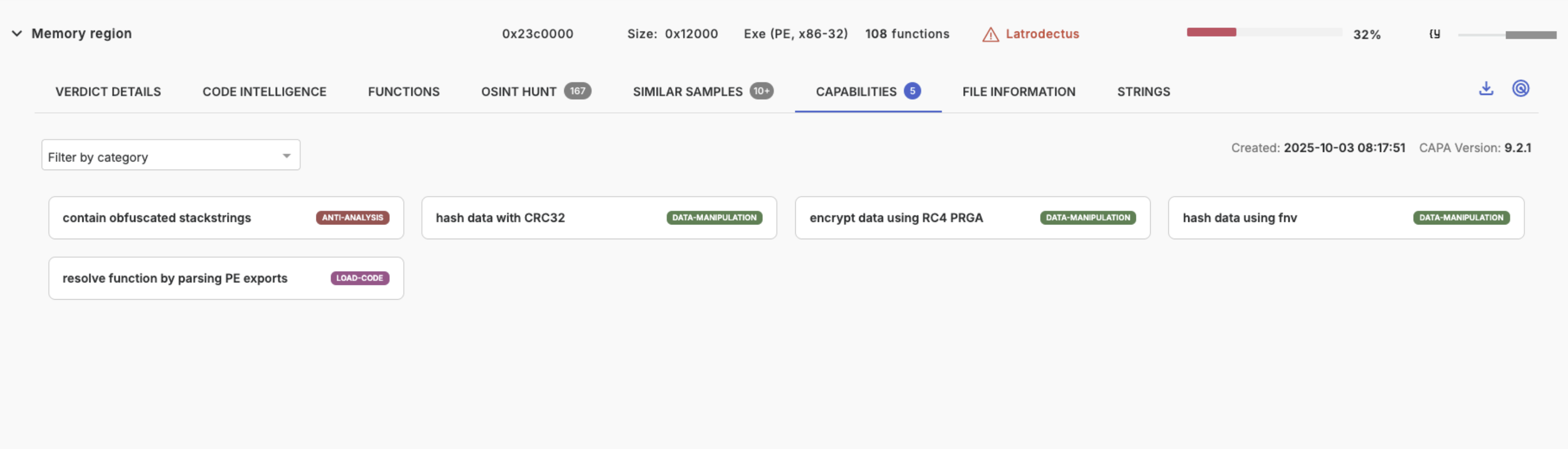
Capabilities
The capabilities tab lists the statically extracted capabilities from this binary code. This is powered by FLARE's capa tool. The functions tab lists these exact capabilities per associated function.
File information
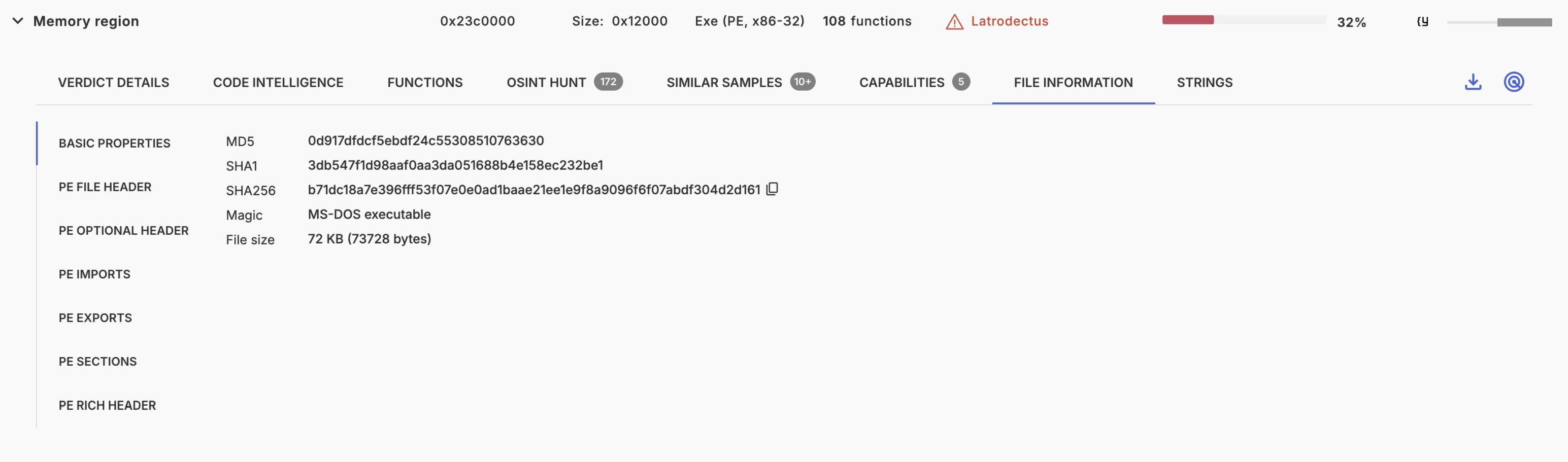
The file information tab lists general file metadata and in case that it is a PE file, PE metadata.
Strings
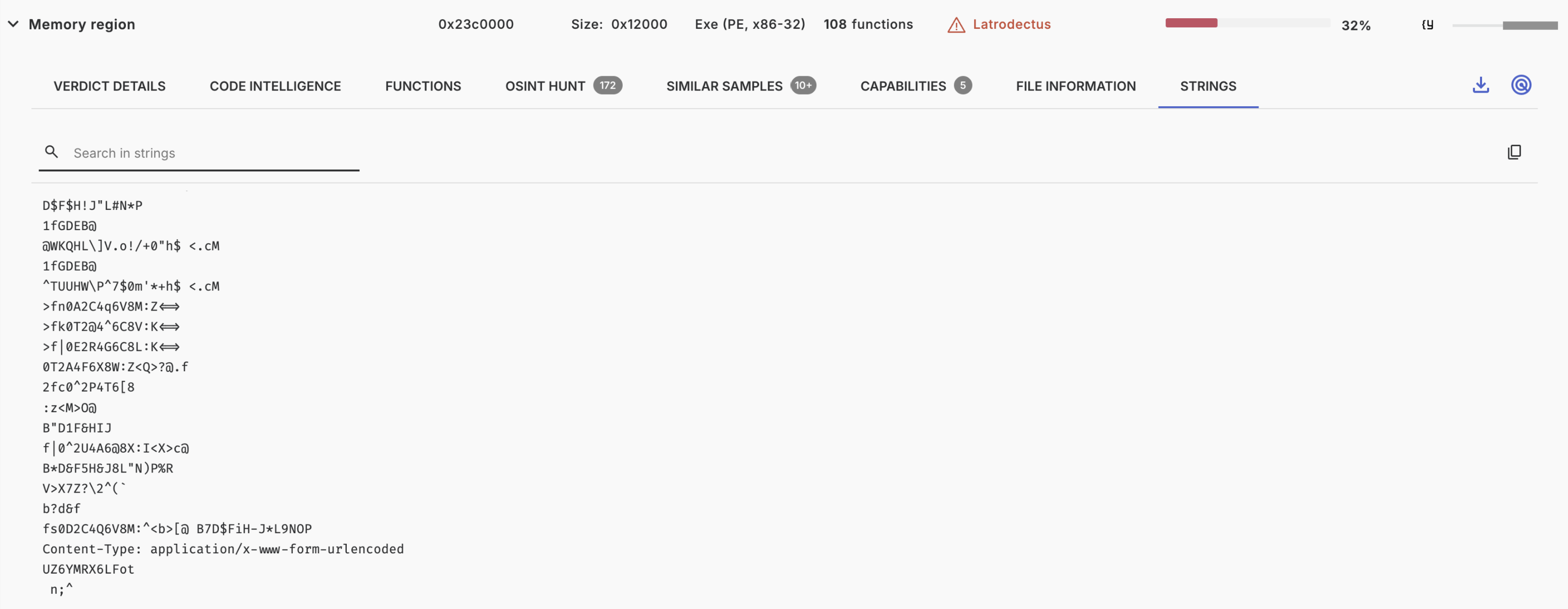
The strings tab lists all strings of the file.
Behavior
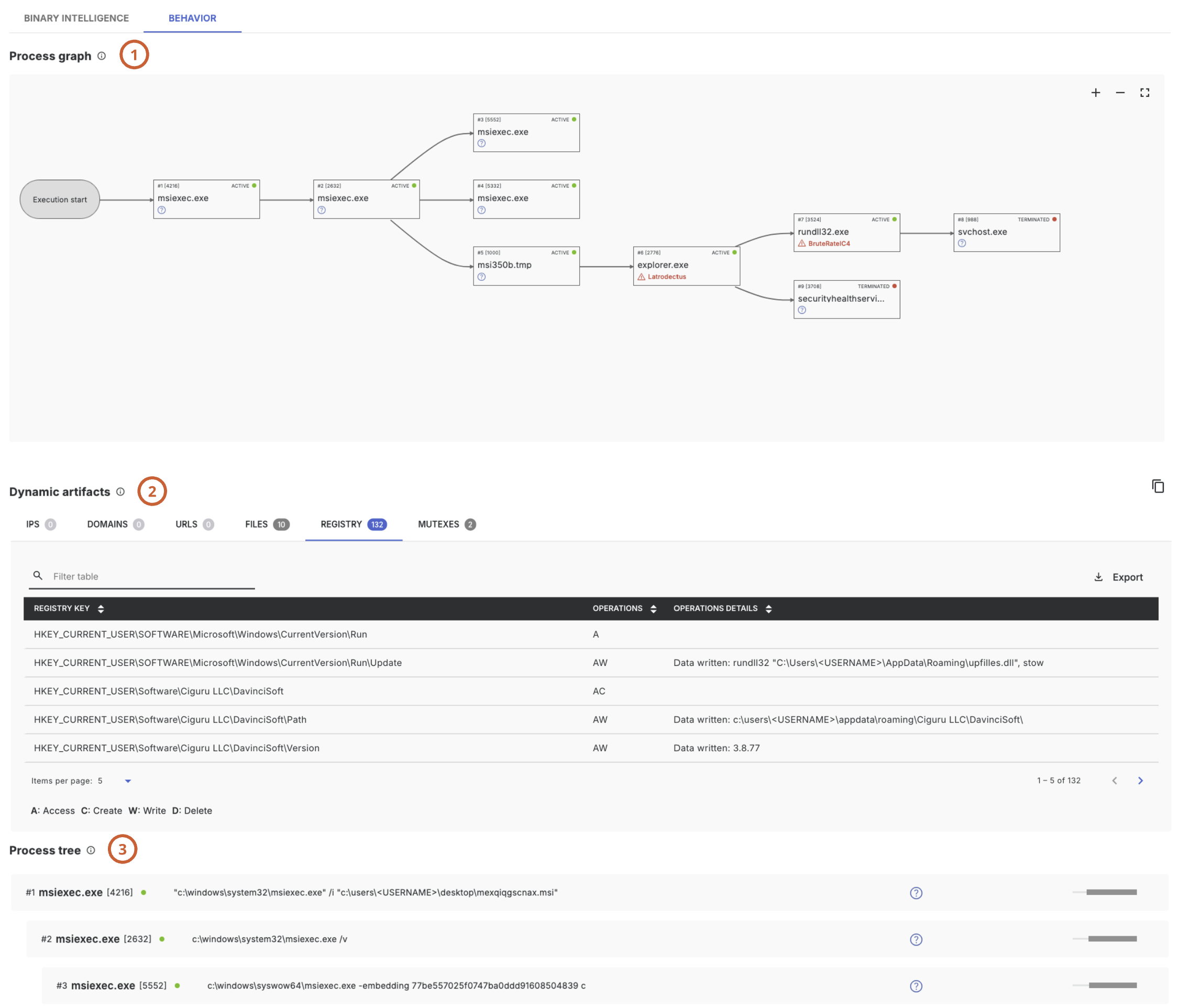
The behavior section contains information from our sandboxing component, such as the process graph (1), dynamic artifacts (2), as well as the process tree (3).
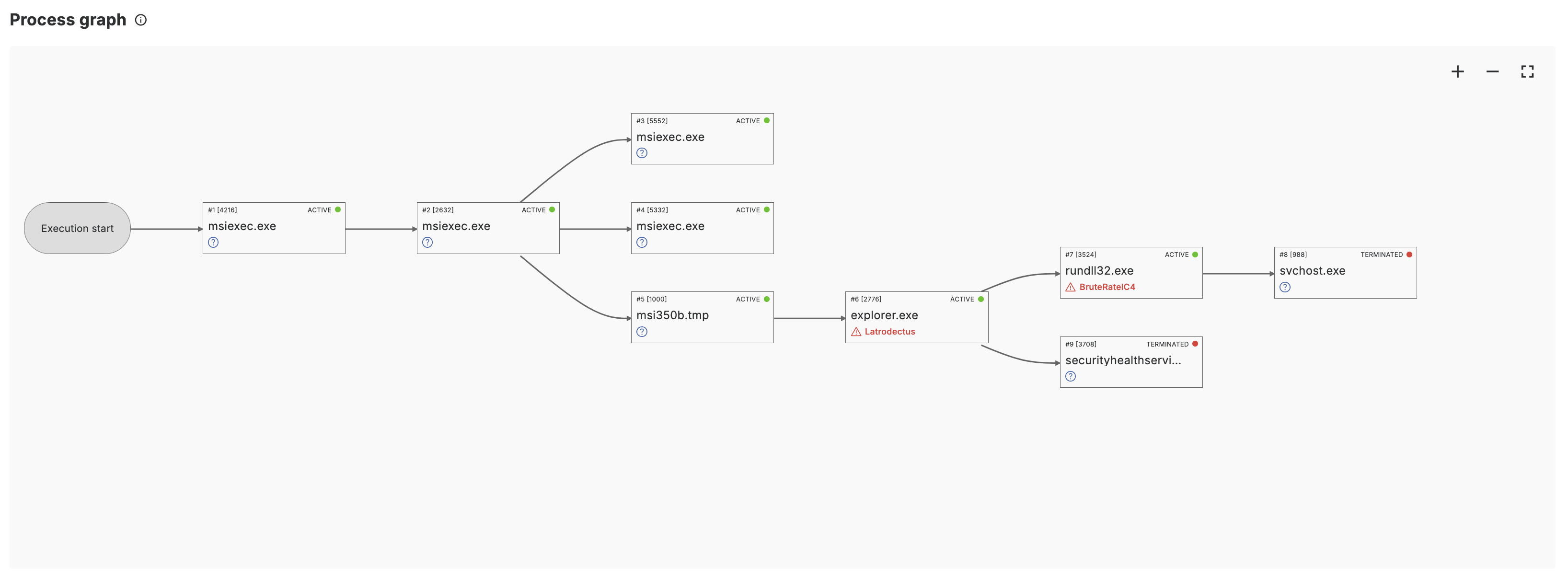
Progress Graph
The process graph shows the process behavior exhibited during the execution of the submitted file in the sandboxing component.
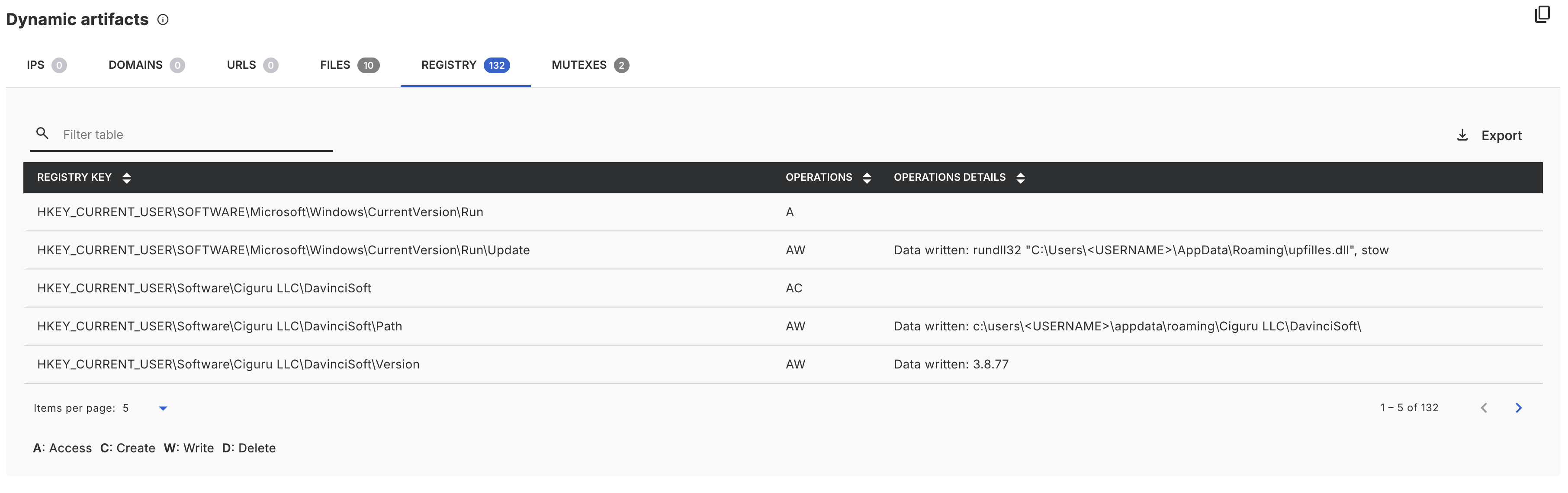
Dynamic Artifacts
The dynamic artifacts section lists all artifacts that were extracted during the sandboxing process. The types collected are:
- IPs, Domains and URLs that were fetched
- Files and registry modifications
- Mutex creations
The extraction process is purely dynamic, no static extraction takes place, e.g. an IP that was not called will not appear here.
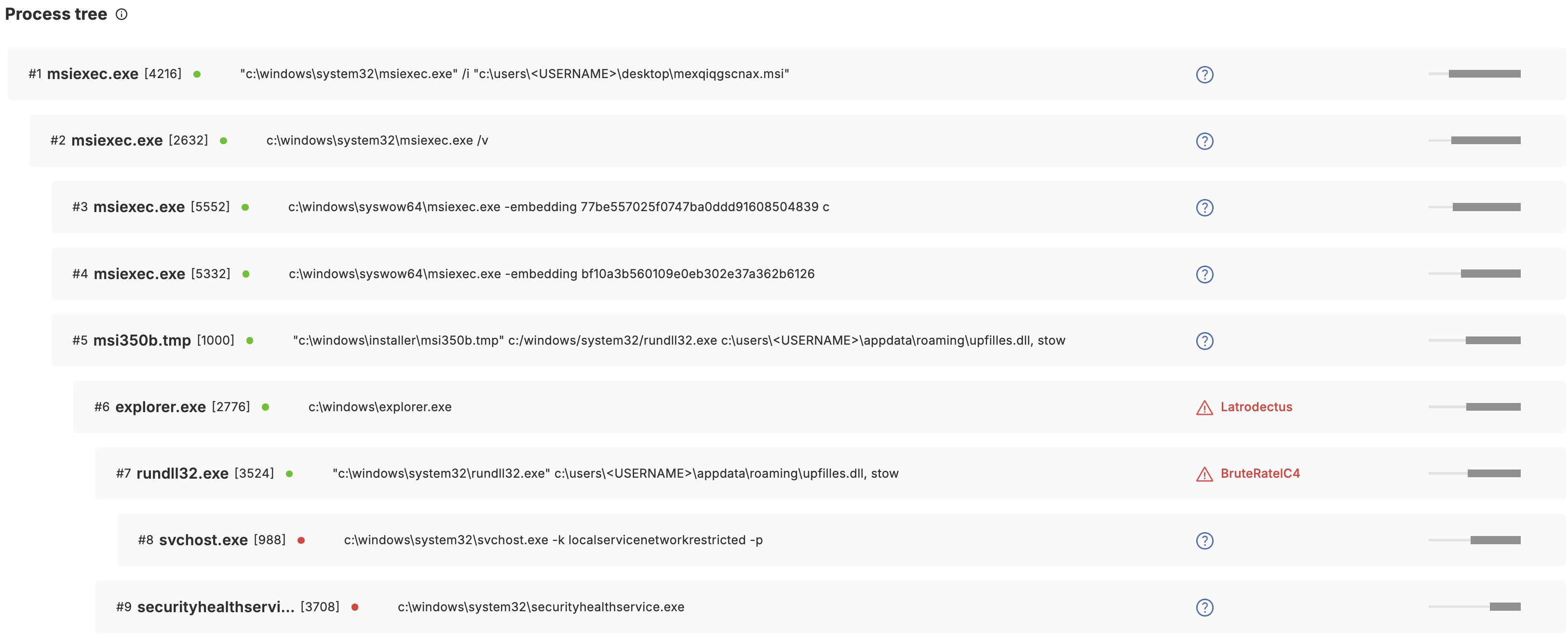
Process Tree
This section shows more details on process behavior, including process name, PID, liveness, command line arguments, verdict and the lifetime.
Updated 4 months ago