IDA Plugin
Threatray provides a plugin for the Hex-Rays IDA Pro disassembler, giving analysts seamless access to Threatray’s binary intelligence capabilities directly within IDA.
The plugin supports IDA 7.6+ on Windows and Linux, requires Python 3.8+, and is available for download here. Installation and usage instructions are included in the README file.
The plugin provides three core functionalities:
Attribute Functions
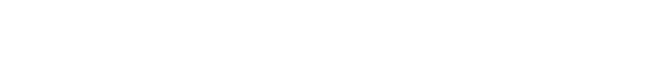
Identify which malware families or libraries functions belong to. The feature shows Threatray's verdict per function in a table (1). Each function can be annotated with a comment, highlighted with color, and renamed to include a detection prefix (2, 3).
This functionality is based on Threatray's code detection technology, as described here.
Retrohunt Functions
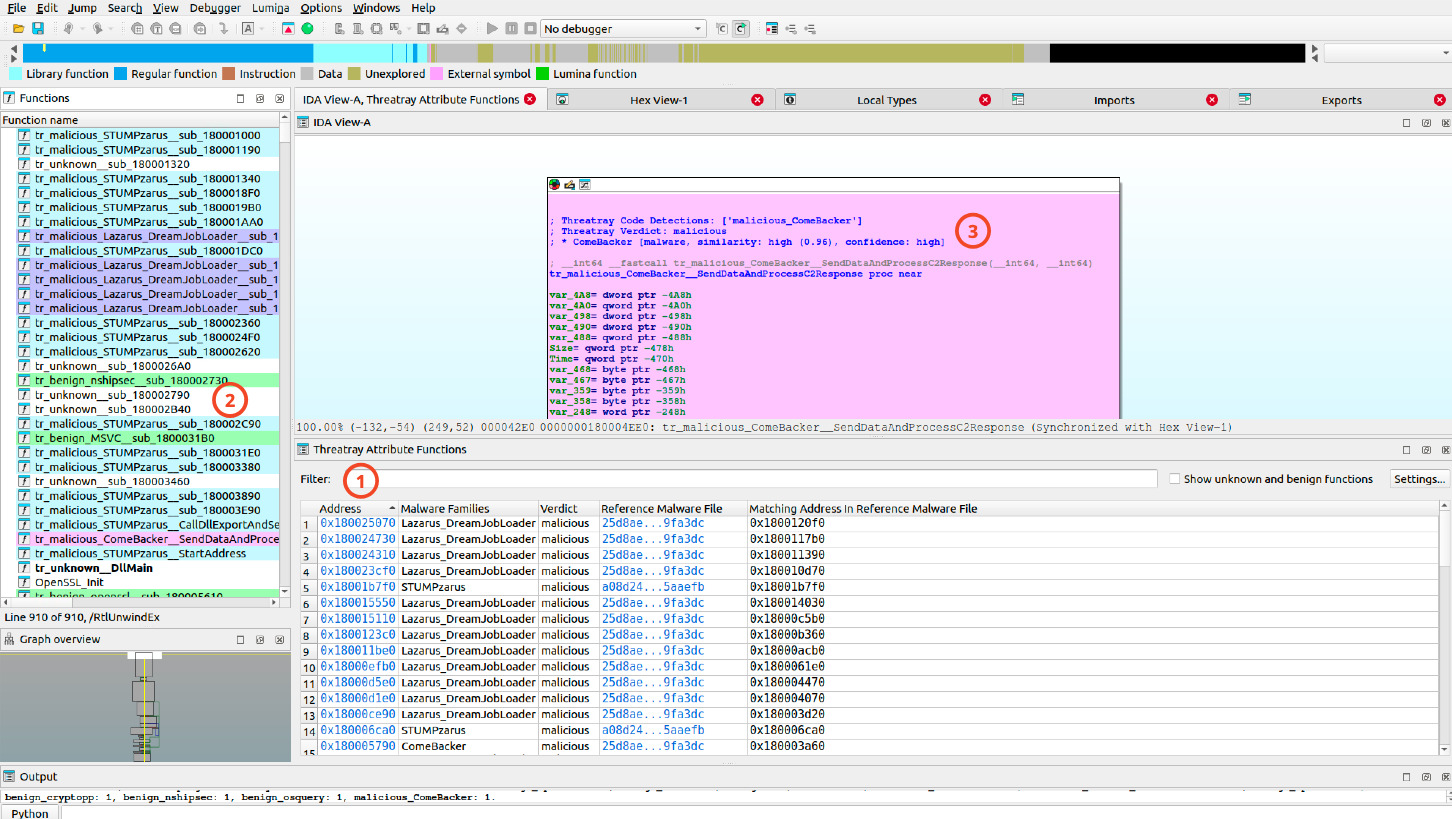
Run a retrohunt on one or multiple functions (1) and display all matching functions, their associated files, and corresponding analyses in Threatray (2).
This functionality is identical to Threatray Retrohunt, but enables free selection of functions directly within IDA.
Find Function Clusters
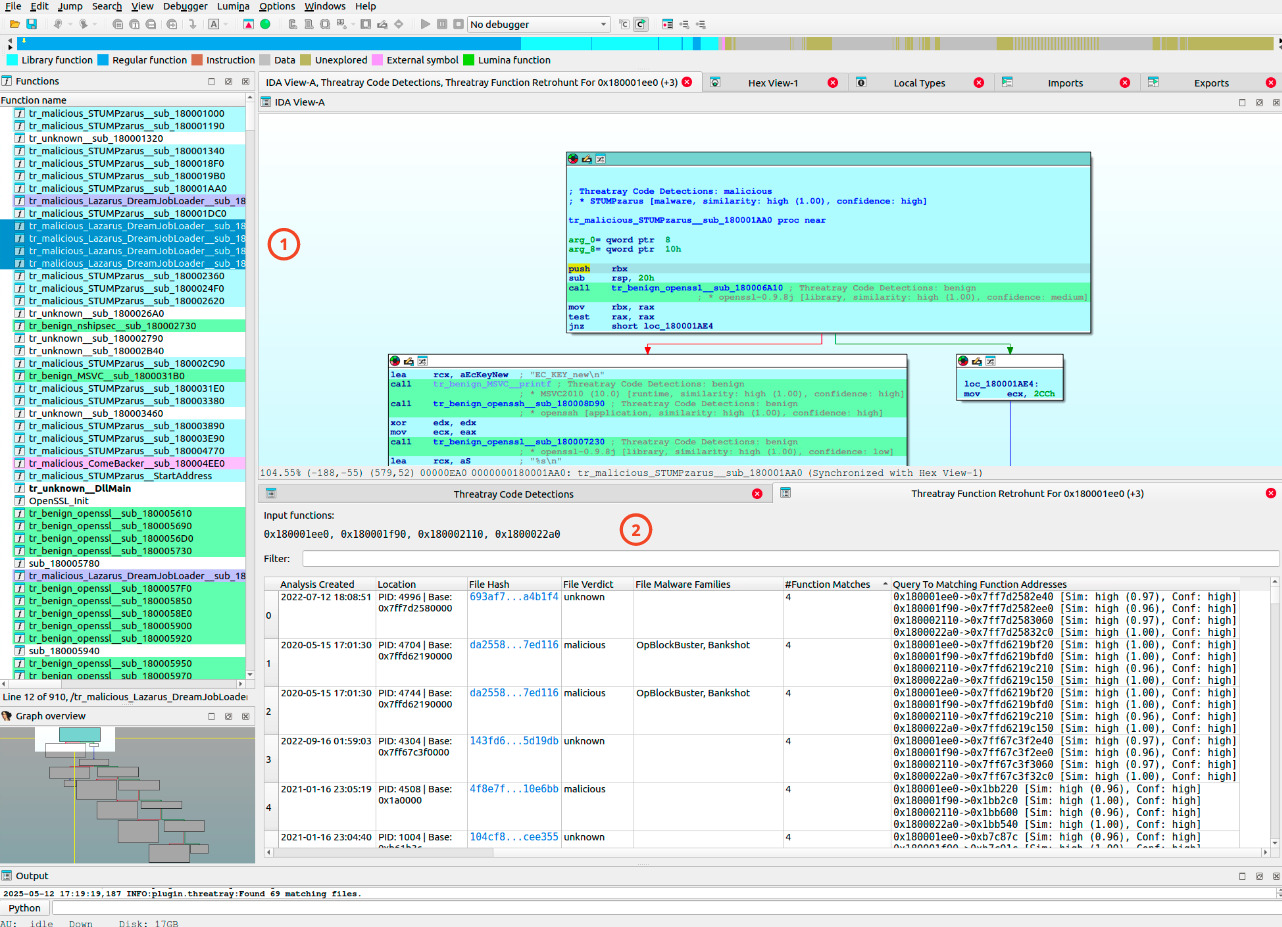
Cluster functions from the file under investigation with functions from a selected set of other files previously analyzed by Threatray (1, 2).
Updated 6 months ago