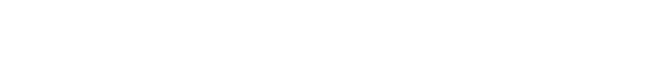
Detection & Identification Verdicts
Threatray verdicts appear throughout an analysis report (such as at the summary, process, and process memory levels) and are accessible via both the UI and the API.
A Threatray verdict combines detection and identification information, following a consistent structure and format. Detection indicates whether a file, entity, etc., is malicious, while identification attributes a file to a specific malware family, such as linking a suspicious DLL to the QakBot malware family. It is important to note that while identification of a malware family implies detection, detection does not necessarily imply identification.
The basics
The detection part of a Threatray verdict is represented by the following symbols:
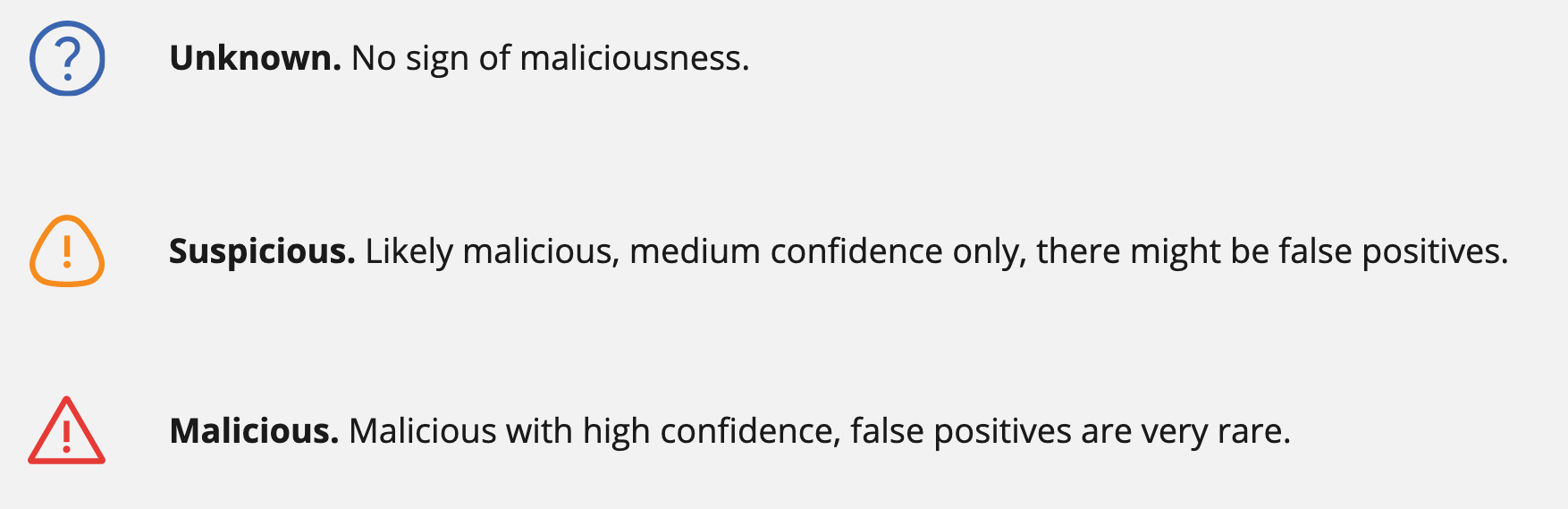
The identification part of a verdict includes one or multiple malware family names. For example, in this instances, such as “Amadey” and “AuroraStealer_Go” in this example:
Verdict details reveal the technologies used to determine the verdict. One is Threatray’s code detection technology, which we use to attribute unknown samples to malware families. In the example above, the malware families “Amadey” and “AuroraStealer_Go” are identified using this technology. In addition, we also independently use an OEM antivirus (AV) engine whose detection verdict (“clean” or “malicious”) is displayed in the verdict details. The AV is not used for family identification.
Threatray tracks thousands of malware families and attack tools, with continuous additions. These include cybercrime, RATs, APTs, hacking tools, and C2 frameworks (e.g., Cobalt Strike, Mimikatz). Primarily, we track payloads, but we also track some loaders and packers. We use Malpedia (https://malpedia.caad.fkie.fraunhofer.de) naming conventions where possible, though we also track families and tools not listed on Malpedia.
Examples
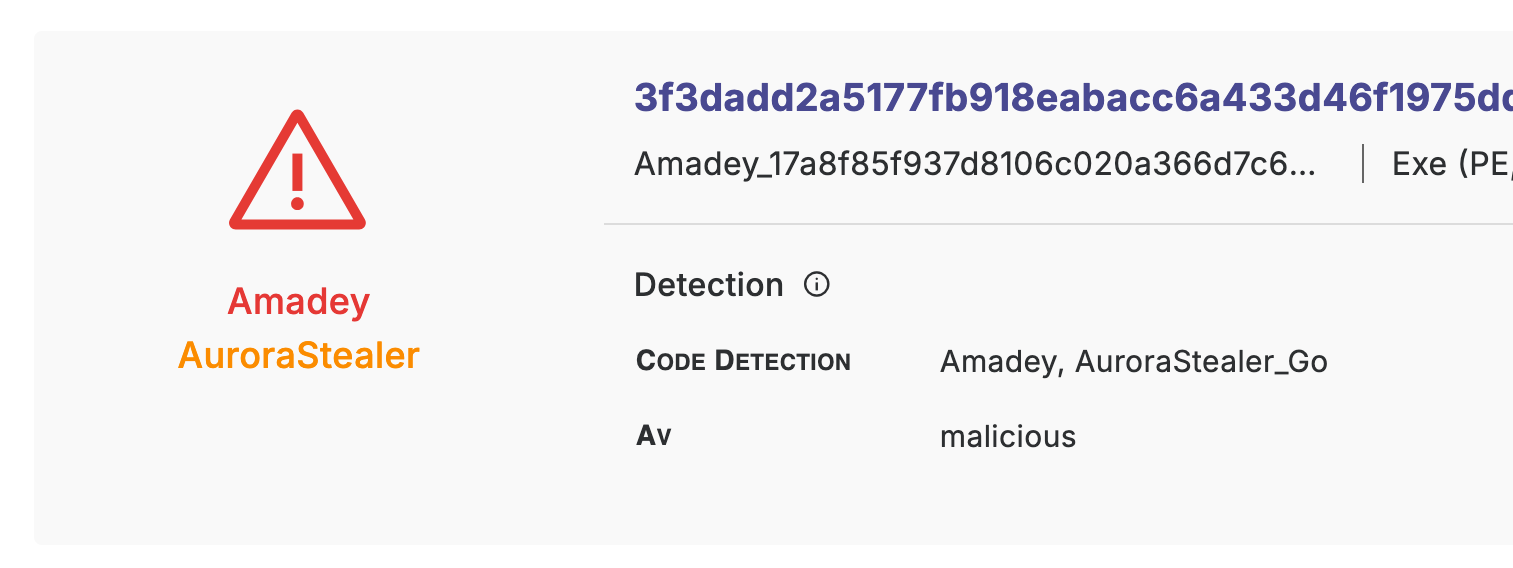
In the example below, we were not able to identify the malware family, but the AV has detected the sample to be malicious, which is why we show the red symbol for malicious files.
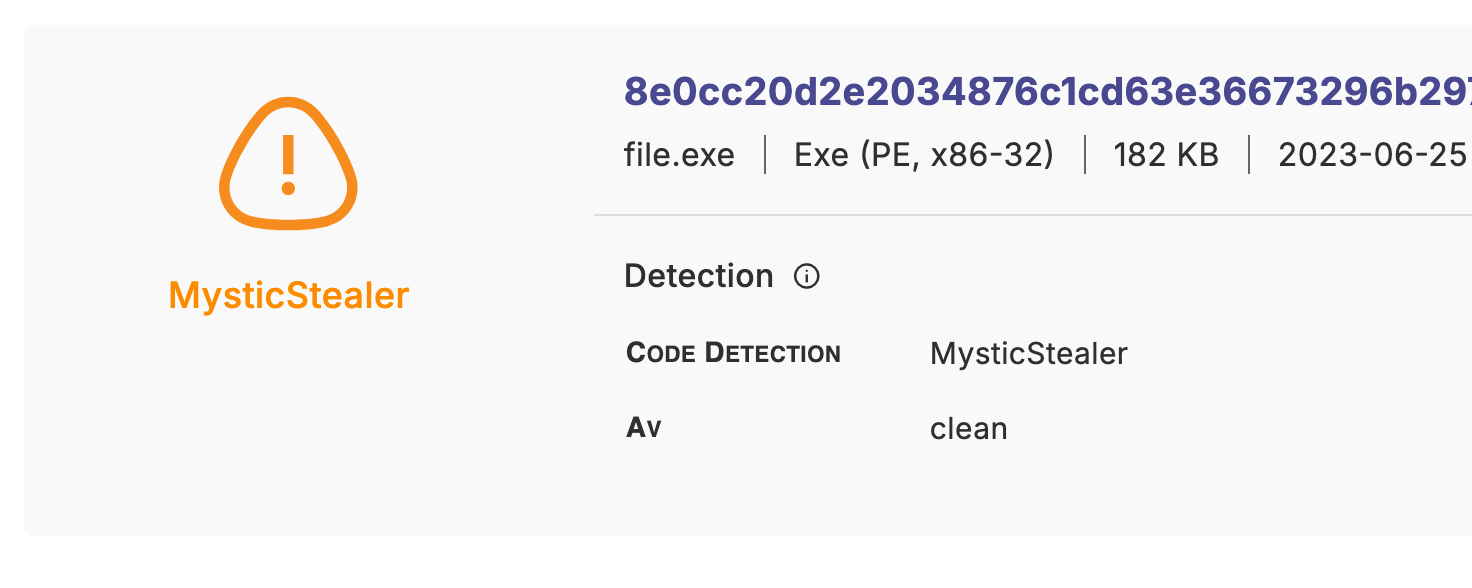
Family names in red, as shown above, signify high confidence, with rare misidentification. Family names in orange indicate medium confidence, with potential for misidentification. In the example below we see a medium confidence attribution to the “DeltaStealer” family:
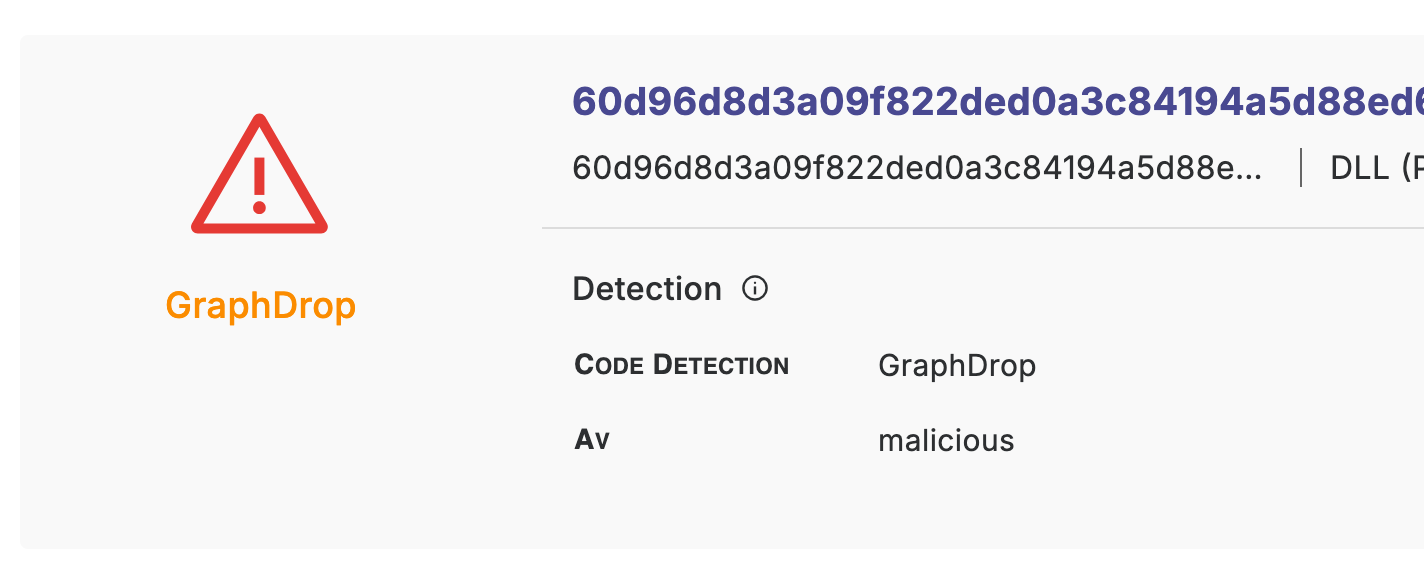
In the example below, we show a high confidence maliciousness (red triangle) and medium confidence attribution to the “GraphDrop” family (orange font):
YARA - community intelligence
We integrate community YARA rules into our system, treating them as independent intelligence pieces. These rules are used "as is" and are not vetted by Threatray. Matches from community do not contribute to detection or intelligence verdicts but are presented separately under ‘intelligence’.
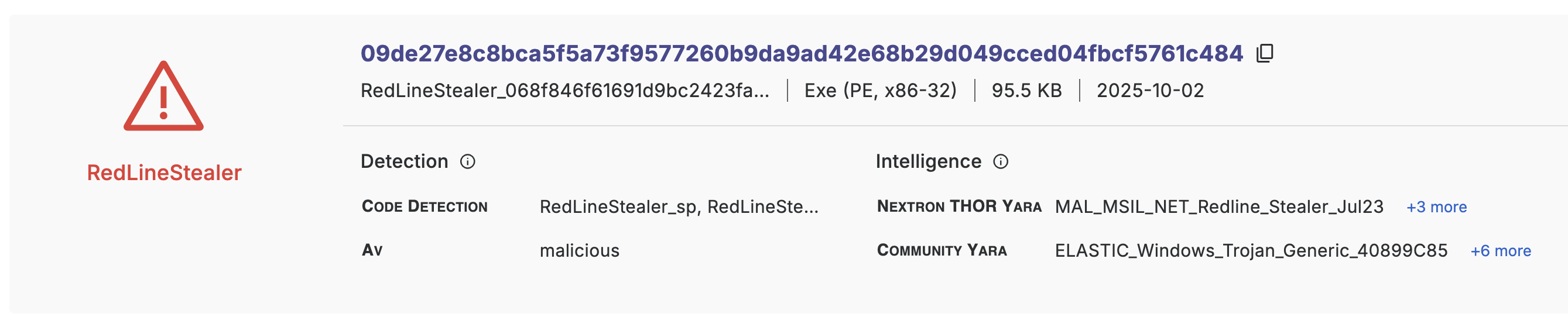
For instance, both a community rule and Threatray’s code detection technology might flag malware as ‘RedLineStealer,’ though different methodologies may sometimes lead to different conclusions.
Updated 4 months ago