Integration with Microsoft Defender for Endpoint Live Response
The endpoint scanner can be launched through Microsoft Defender for Endpoint (MDE).
Before proceeding, ensure that live response is enabled. Follow the steps detailed in the official documentation at https://docs.microsoft.com. It is required to Enable live response unsigned script execution, as outlined in the provided guide.
Add the Powershell script to the live response library
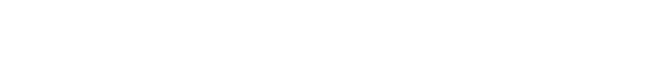
Begin by accessing the Threatray UI to download the endpoint scanner binary provided as a PowerShell script. This script contains the binary in Base64 encoded form and will decode and execute it upon running the script.
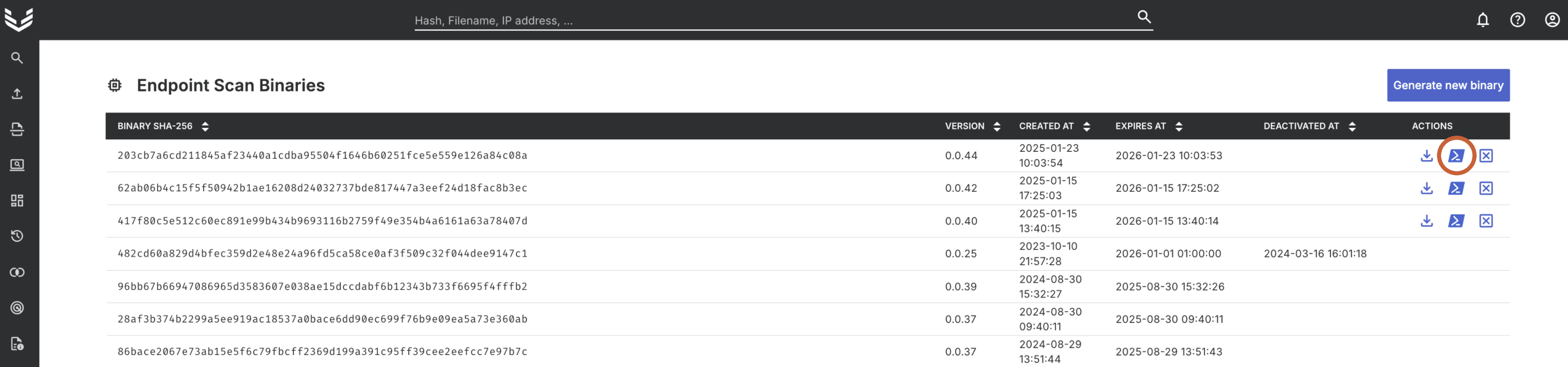
Next, create a new live response session to any host to add the Powershell script to the library.
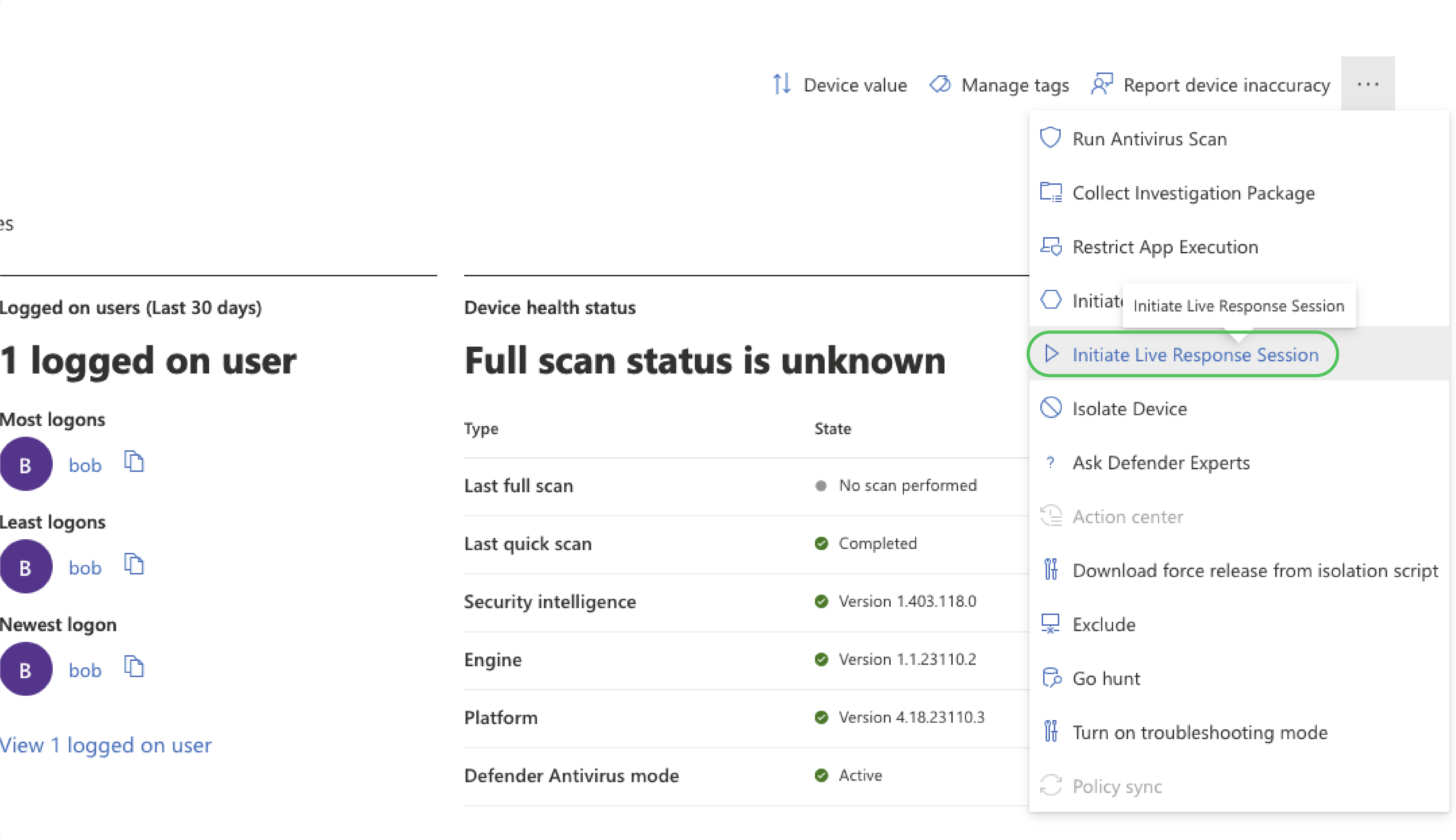
Proceed by opening the upload dialog and uploading the threatray_endpoint_scan.ps1 script. Opt for Overwrite file if replacing any existing versions of the script.
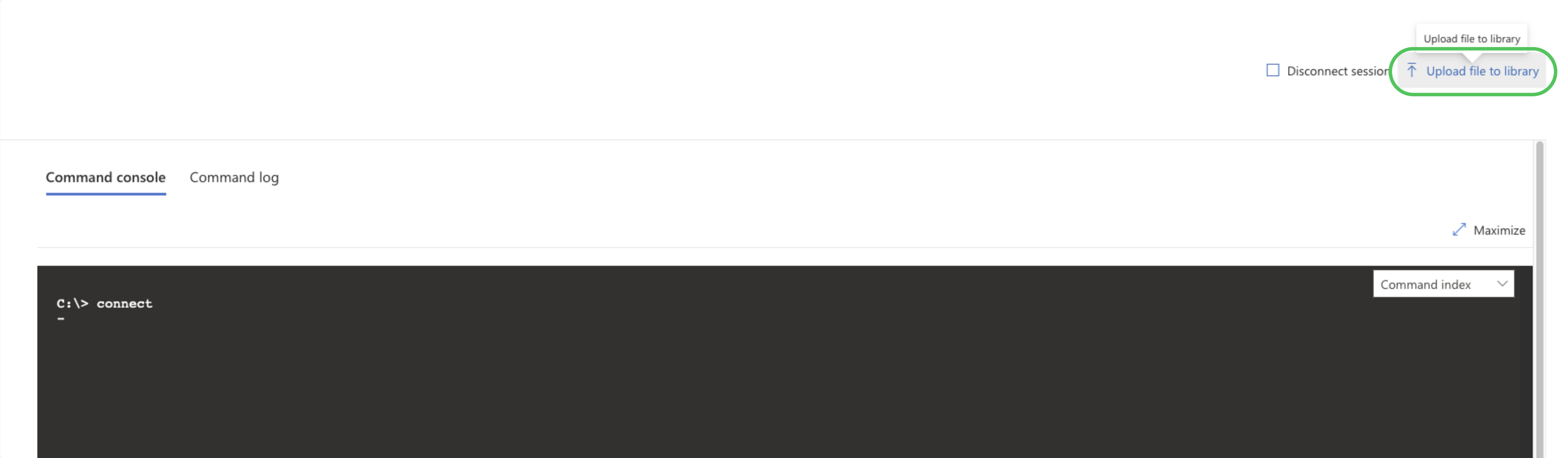
Once uploaded, the script becomes accessible in the live response library. To view it, type library within the session.
Running a live response session
Initiate a live response session for the target host you intend to scan.
Execute the script, optionally adding command line parameters using -parameters "". For example:
run threatray_endpoint_scan.ps1 -parameters "/disable-ssl-verification /processes-to-ignore lsass.exe"After a short while, the scan’s log output will be displayed in the live response console, resembling the example below:
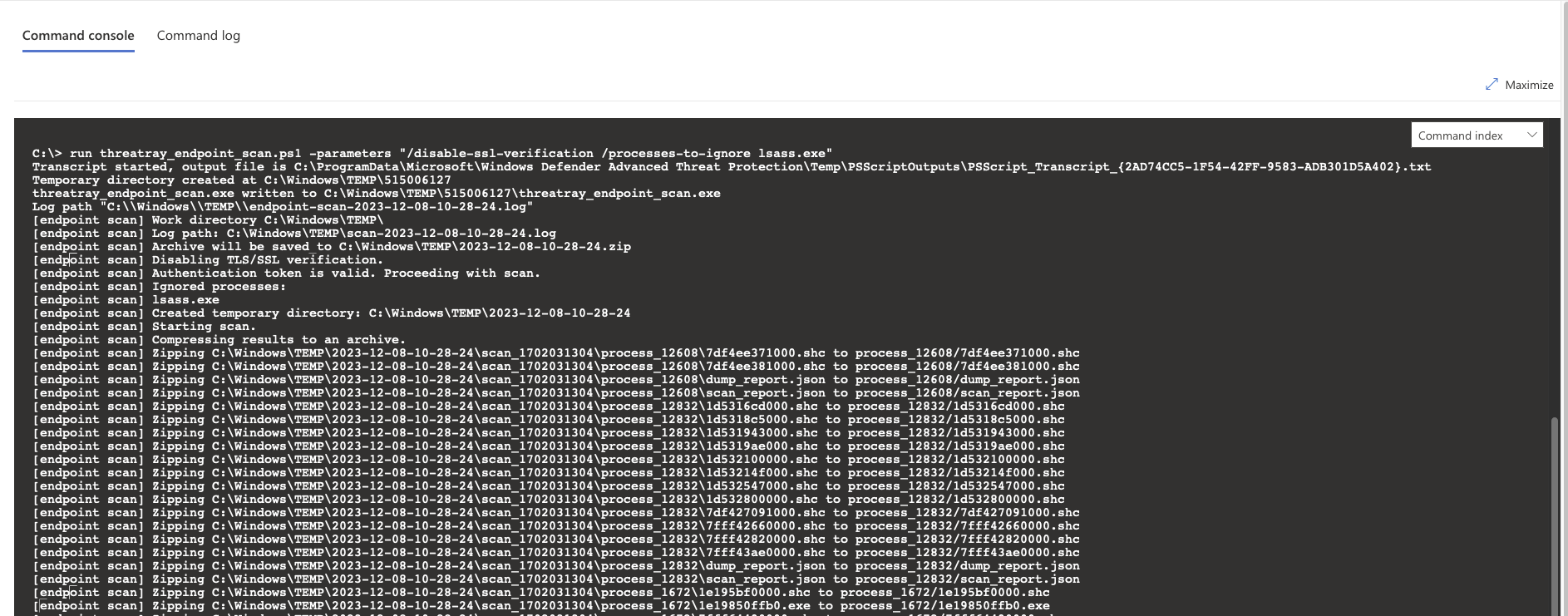
At this point, the analysis results will be accessible in your Threatray instance.
Running a live response session on a host with restricted internet
If an endpoint lacks access to *.threatray.com:443, you can execute the endpoint scan without uploading the created archive using the /skip-upload flag. Subsequently, fetch the archive using the getfile command from the live response console. Optionally provide the /archive-file-path parameter, which can be used to specify the archive file location in combination with getfile. Alternatively, retrieve the archive file path from the console output of the endpoint scan.
For example:
run threatray_endpoint_scan.ps1 -parameters "/skip-upload /archive-file-path c:\temp\scan\threatray-endpoint-scan-archive.zip"
getfile c:\temp\scan\threatray-endpoint-scan-archive.zipWith the output as follows:
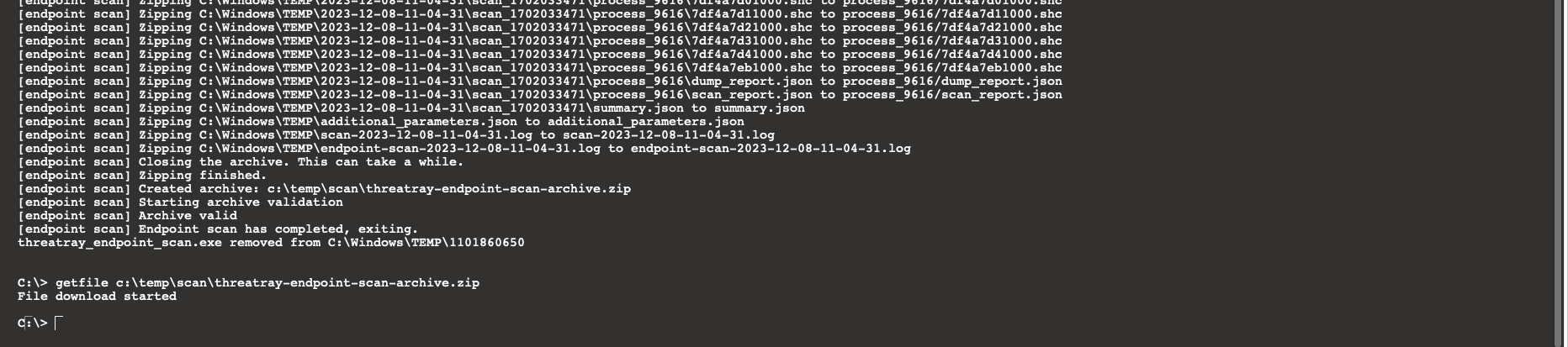
The fetched archive will appear as a new download in the console and can be submitted to Threatray for analysis.
Updated 4 months ago