OSINT Hunt
OSINT Hunt can identify code-wise similar samples mentioned in open-source intelligence (OSINT) reports.
Traditional methods of finding OSINT related to a sample, such as searching for hashes, IP addresses, or other indicators on Google or intelligence databases, often fall short. Attackers routinely change these indicators between campaigns, making it difficult to link new malware to previously published OSINT.
In contrast, malware code often remains at least partially the same between campaigns. OSINT Hunt leverages this by using the same technology as Retrohunt, explained here, to conduct fast and deep searches, delivering more precise results than traditional methods. The primary difference to Retrohunt is that OSINT Hunt limits its search scope to samples mentioned in OSINT reports.
Threatray continuously collects and ingests OSINT reports from various sources, including cybersecurity blog posts, tweets, and curated malware repositories. These reports are processed, with summaries and file hashes extracted and made accessible to the user. For each file hash mentioned in the report, Threatray attempts to find and download the actual file for analysis, enabling the OSINT Hunt feature to relate a sample under inspection to samples mentioned in reports.
OSINT Hunt is available for any piece of binary code, such as a submitted file or memory region, via a dedicated tab (1).
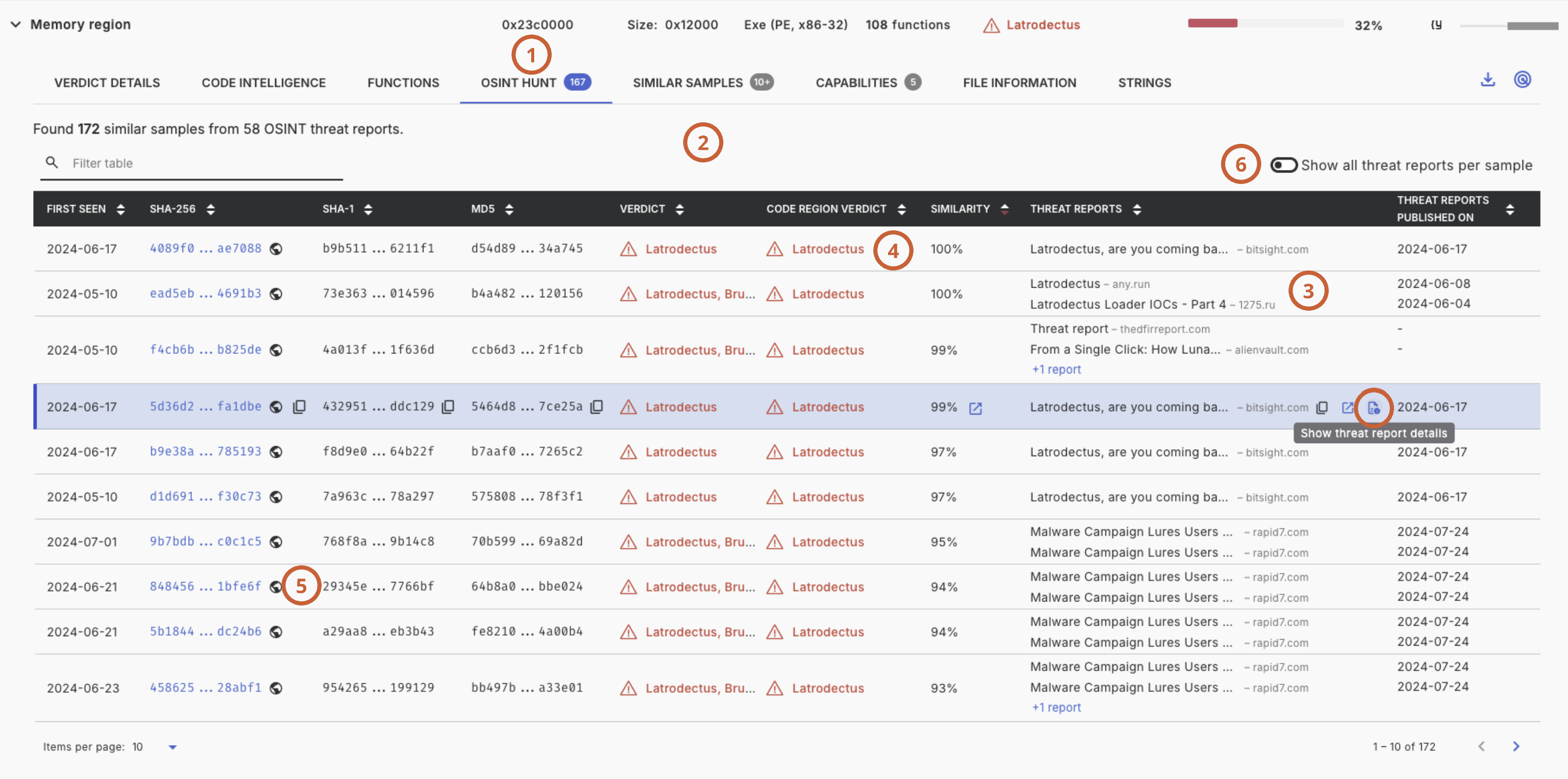
The resulting list displays similar samples (2) mentioned by hash in OSINT reports (3), sorted by similarity score. If the sample under inspection was mentioned directly by hash, it is indicated with the term 'hash-equal' (4). All three commonly used hashes are listed (5), as reports may use any of them to indicate the file. Since each sample could appear in multiple reports, a switch at the top allows users to show all reports (6) mentioning the sample.
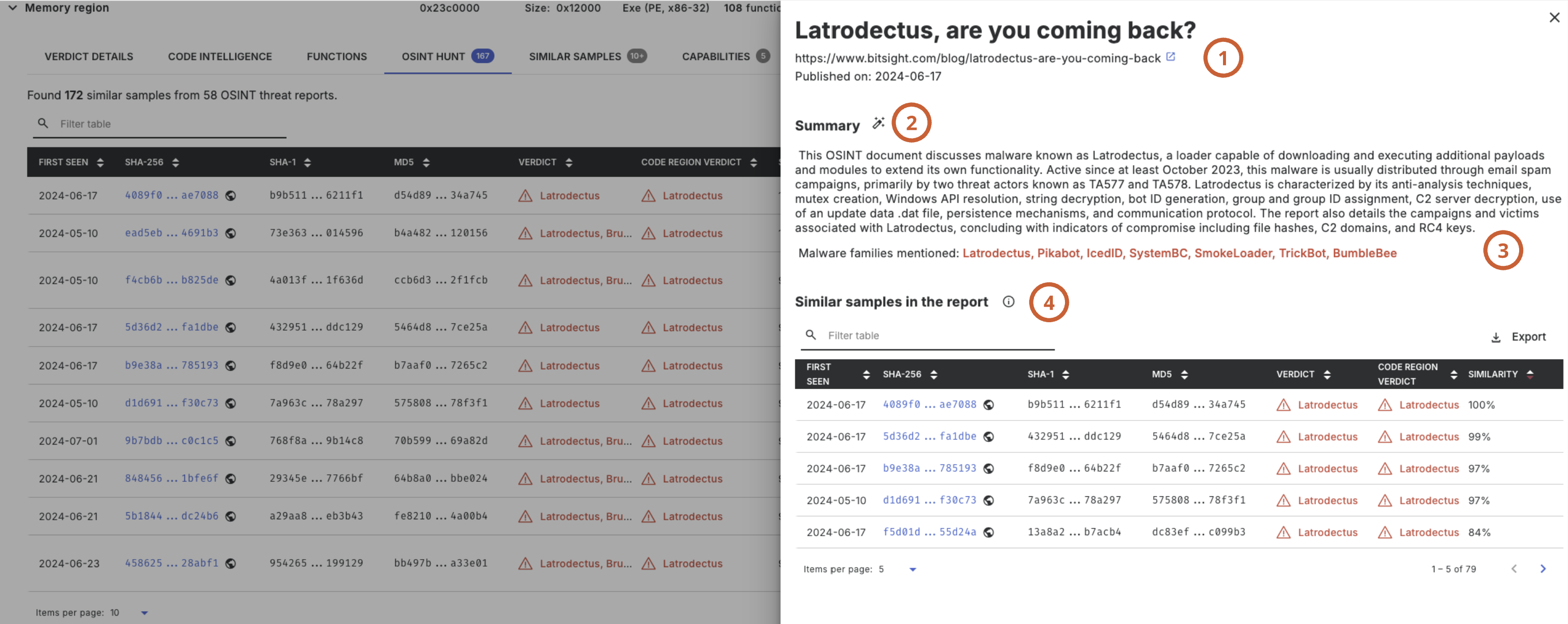
Each report can be opened to display its details, including metadata (1), an LLM-generated summary (2), and the mentioned malware families (3).
The similar samples found and analyzed by Threatray are listed below (4).
Updated 4 months ago