Integration with Velociraptor
The endpoint scan binary can be integrated into Velociraptor through two available artifacts:
Windows.Scanner.Threatray: Ideal for standard endpoint scans where the endpoint autonomously uploads data to your private Threatray instance.Windows.Scanner.ThreatrayArchive: Ideal for scanning endpoints without access to*threatray.com:443. This artifact retrieves the created archive to the Velociraptor server. Subsequently, it’s the operator’s responsibility to manually upload the archive to the Threatray instance, either via the UI or API.
Add the artifacts to the server
Create a new artifact by navigating to the artifacts page and clicking the Add an Artifact button.
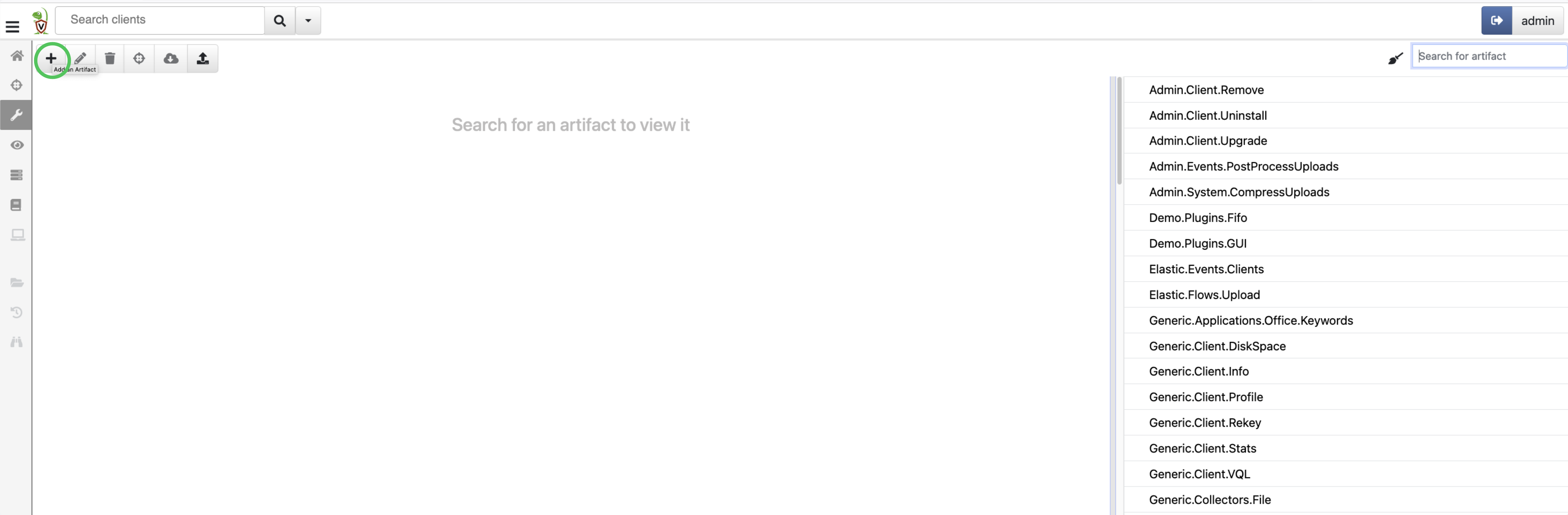
Paste in the following code and create the artifact:
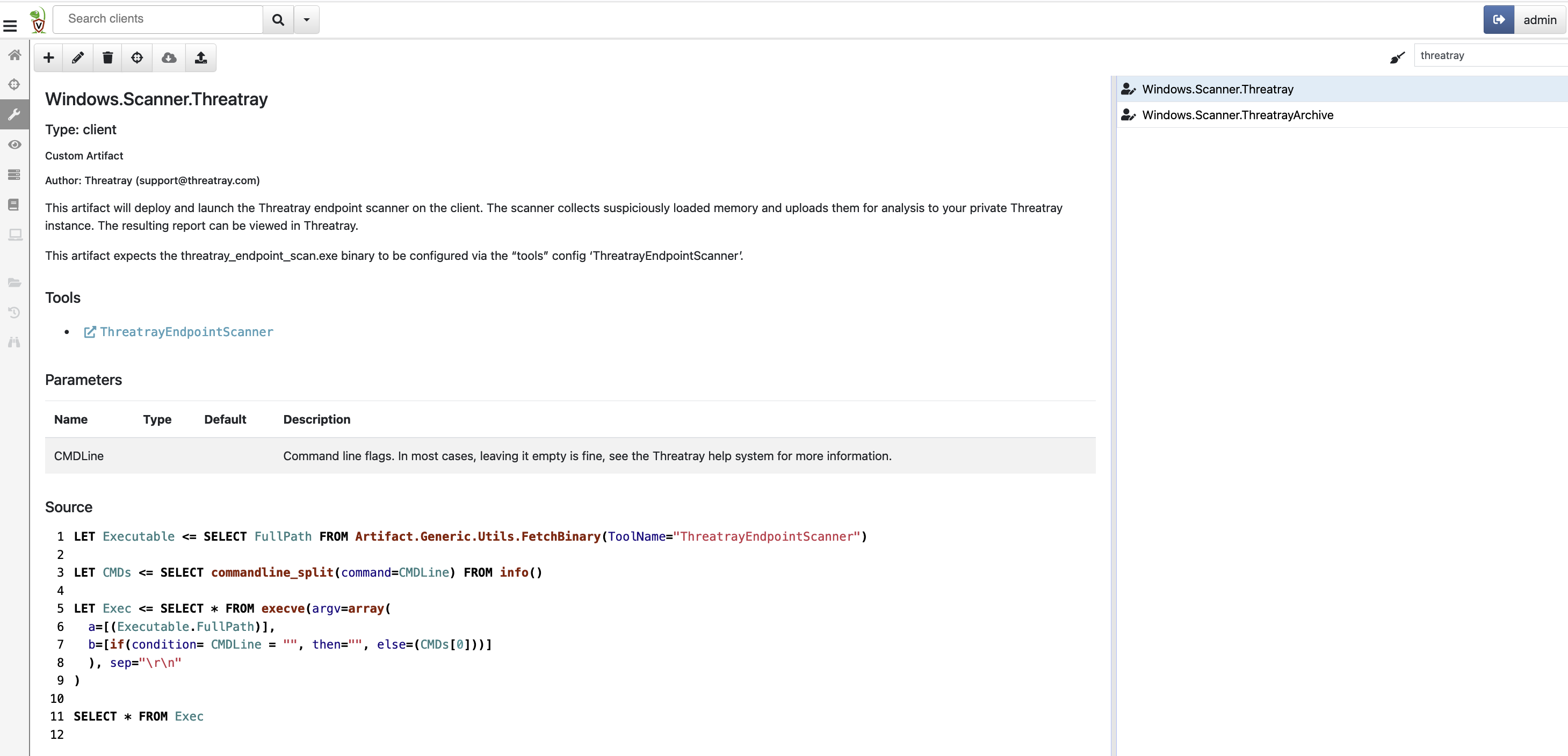
name: Windows.Scanner.Threatray
description: |
This artifact will deploy and launch the Threatray endpoint scanner on the client.
The scanner collects suspiciously loaded memory and uploads them for analysis to
your private Threatray instance. The resulting report can be viewed in Threatray.
<br />
This artifact expects the threatray_endpoint_scan.exe binary to be configured via the "tools" config
'ThreatrayEndpointScan'.
author: Threatray ([email protected])
tools:
- name: ThreatrayEndpointScan
type: CLIENT
required_permissions:
- EXECVE
precondition: SELECT OS From info() where OS = 'windows' AND Architecture = 'amd64'
parameters:
- name: CMDLine
description: Command line flags. In most cases, leaving it empty is fine, see the Threatray help system for more information.
default: ""
sources:
- query: |
LET Executable <= SELECT * FROM Artifact.Generic.Utils.FetchBinary(ToolName="ThreatrayEndpointScan", TemporaryOnly=true)
LET CMDs <= SELECT commandline_split(command=CMDLine) FROM info()
LET Exec <= SELECT * FROM execve(argv=array(
a=[(Executable.OSPath[0])],
b=[if(condition= CMDLine = "", then="", else=(CMDs[0]))]
), sep="\r\n"
)
SELECT * FROM ExecIt should look as follows:
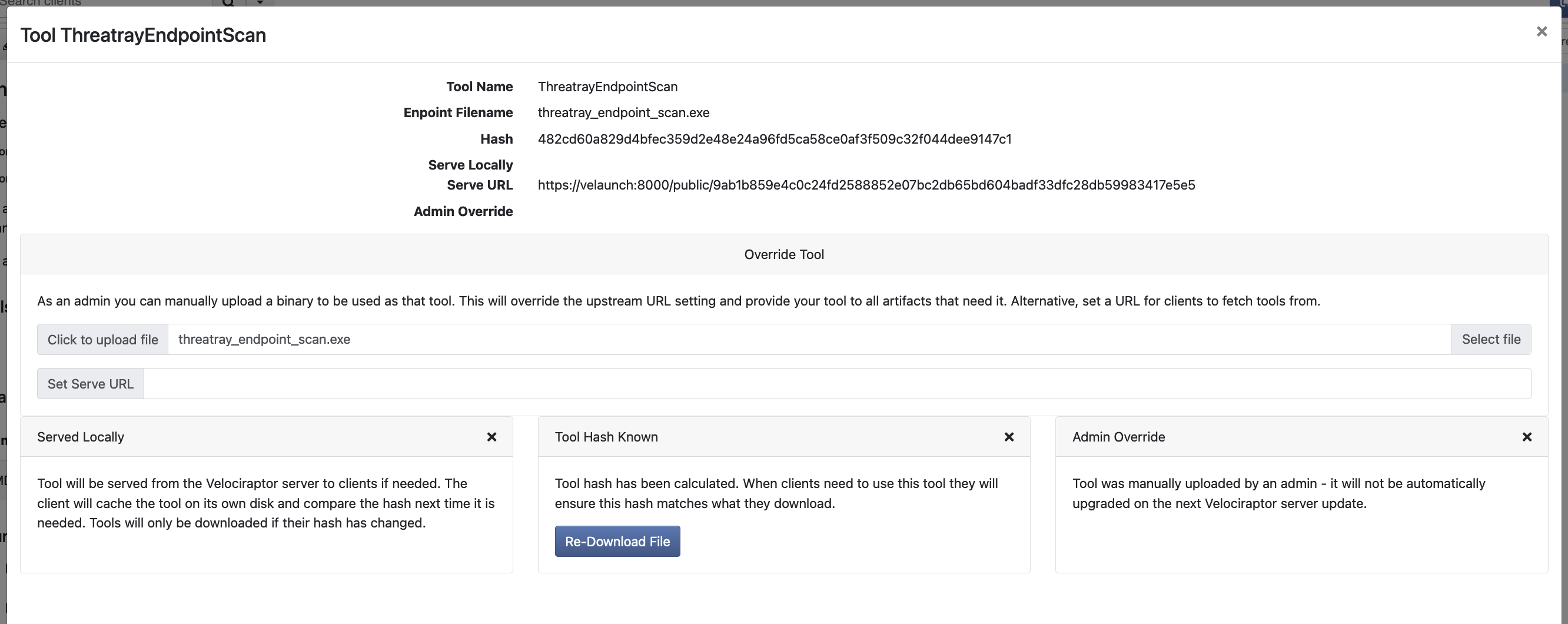
Click on the Tools -> ThreatrayEndpointScan button and upload the threatray_endpoint_scan.exe binary that you’ve downloaded from Threatray and confirm by clicking the Click to upload file button.
Repeat the same steps with the Windows.Scanner.ThreatrayArchive artifact. The upload threatray_endpoint_scan.exe binary step can be skipped.
name: Windows.Scanner.ThreatrayArchive
description: |
This artifact will deploy and launch the Threatray endpoint scanner on the client.
The scanner collects suspiciously loaded memory and uploads them for analysis to
your private Threatray instance. The resulting report can be viewed in Threatray.
<br />
This artifact expects the threatray_endpoint_scan.exe binary to be configured via the "tools" config
'ThreatrayEndpointScan'.
author: Threatray ([email protected])
tools:
- name: ThreatrayEndpointScan
type: CLIENT
required_permissions:
- EXECVE
precondition: SELECT OS From info() where OS = 'windows' AND Architecture = 'amd64'
parameters:
- name: CMDLine
description: Command line flags. In most cases, leaving it empty is fine, see the Threatray help system for more information.
default: ""
sources:
- query: |
LET Executable <= SELECT * FROM Artifact.Generic.Utils.FetchBinary(ToolName="ThreatrayEndpointScan", TemporaryOnly=true)
LET CMDs <= SELECT commandline_split(command=CMDLine) FROM info()
LET Tempfile <= tempdir(remove_last=TRUE) + "\\threatray-endpoint-scan-archive.zip"
LET Exec <= SELECT * FROM execve(argv=array(
a=[(Executable.OSPath[0]), "/skip-upload", "/archive-file-path", Tempfile],
b=[if(condition= CMDLine = "", then="", else=(CMDs[0]))]
), sep="\r\n"
)
LET Upload <= upload(file=Tempfile, name="threatray-endpoint-scan-archive.zip")
SELECT * FROM Exec
If you have already added the Threatray artifacts in the past, and would like to change or update them, then select them in the list of artifacts and click the Edit an Artifact button.
Hunting with the artifact
Now you can run a new hunt with the Windows.Scanner.Threatray or Windows.Scanner.ThreatrayArchive artifacts. The subsequent screenshots show how to launch an example hunt.
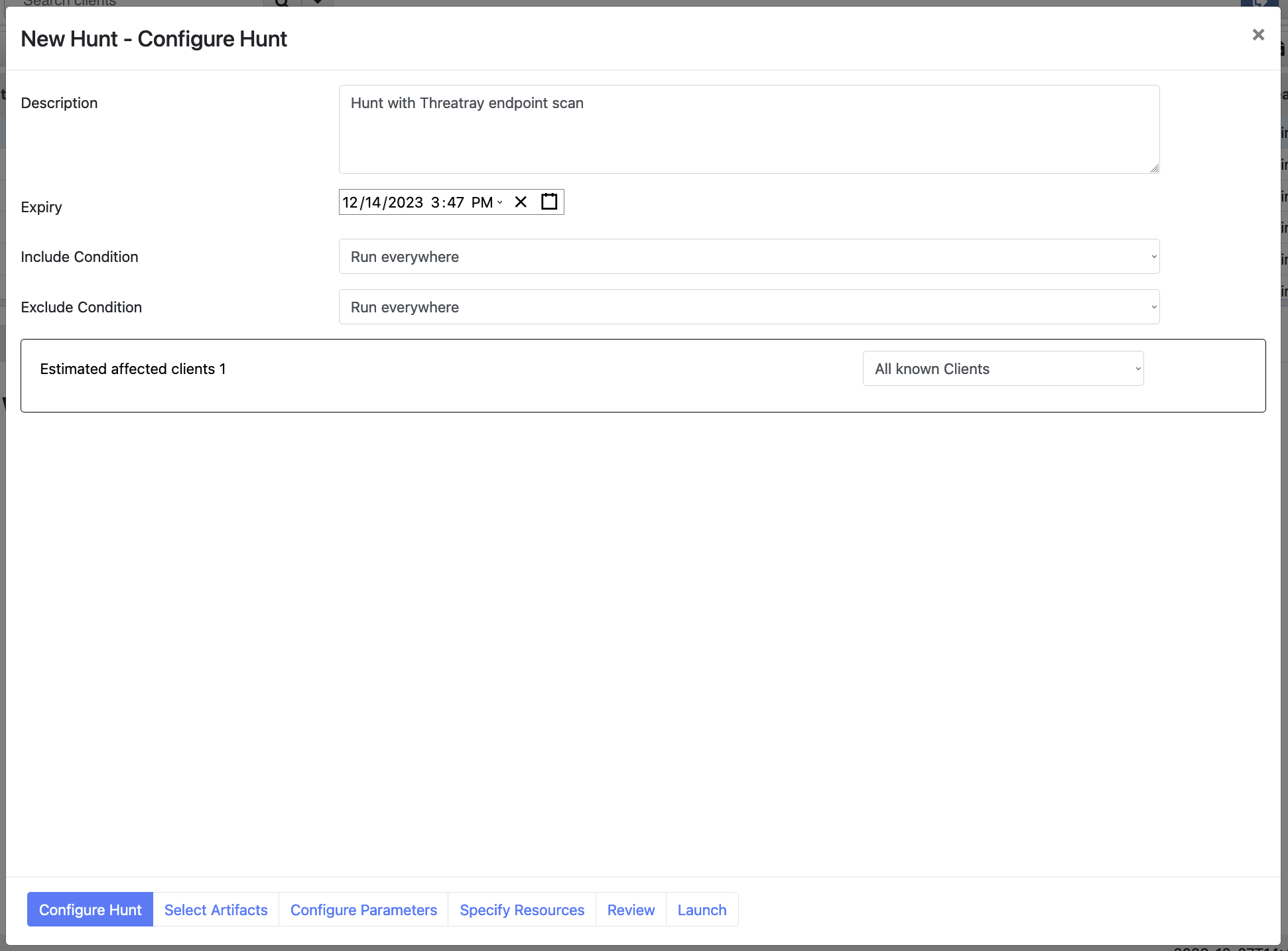
Create a new hunt.
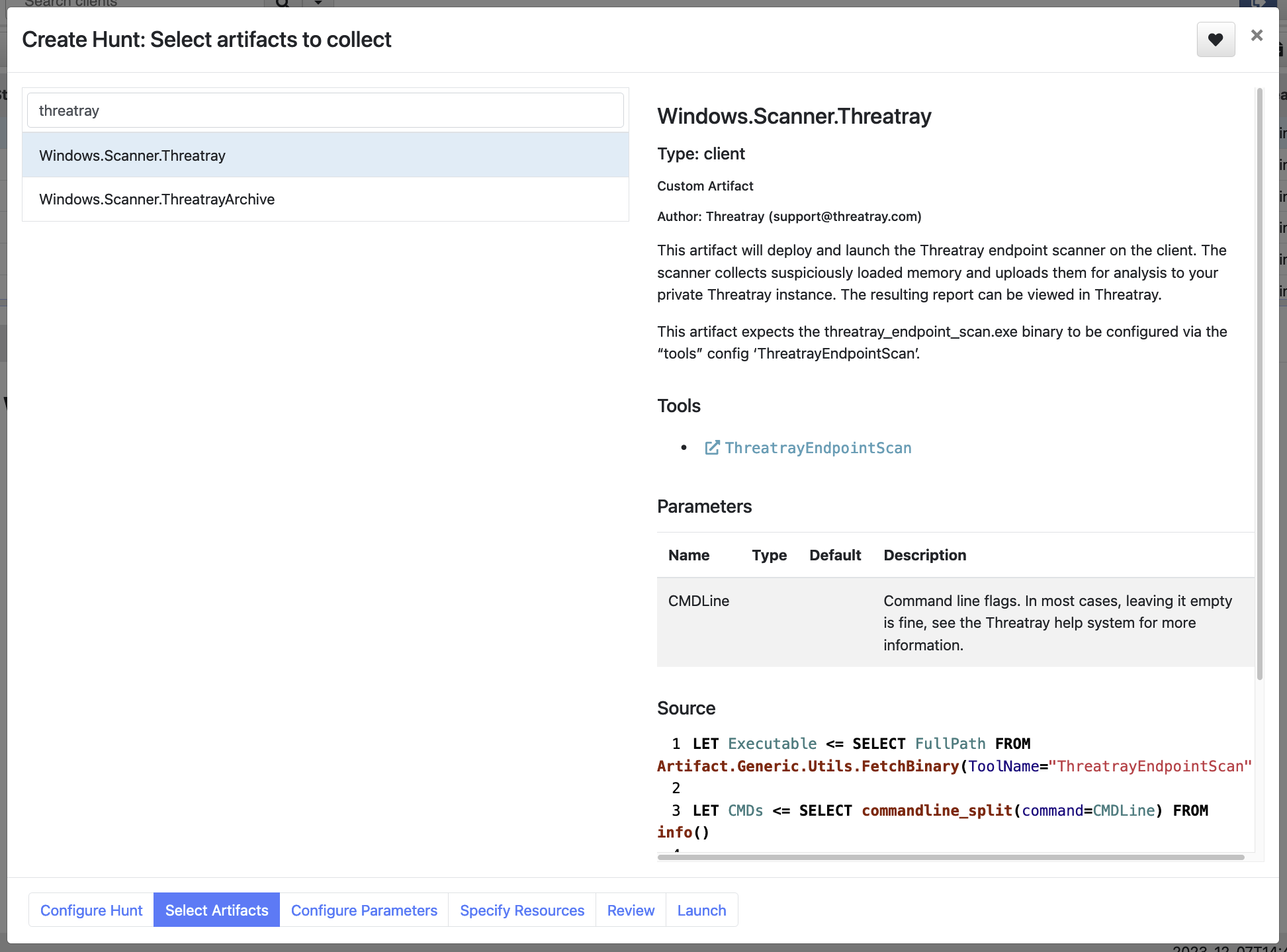
The chosen artifact.
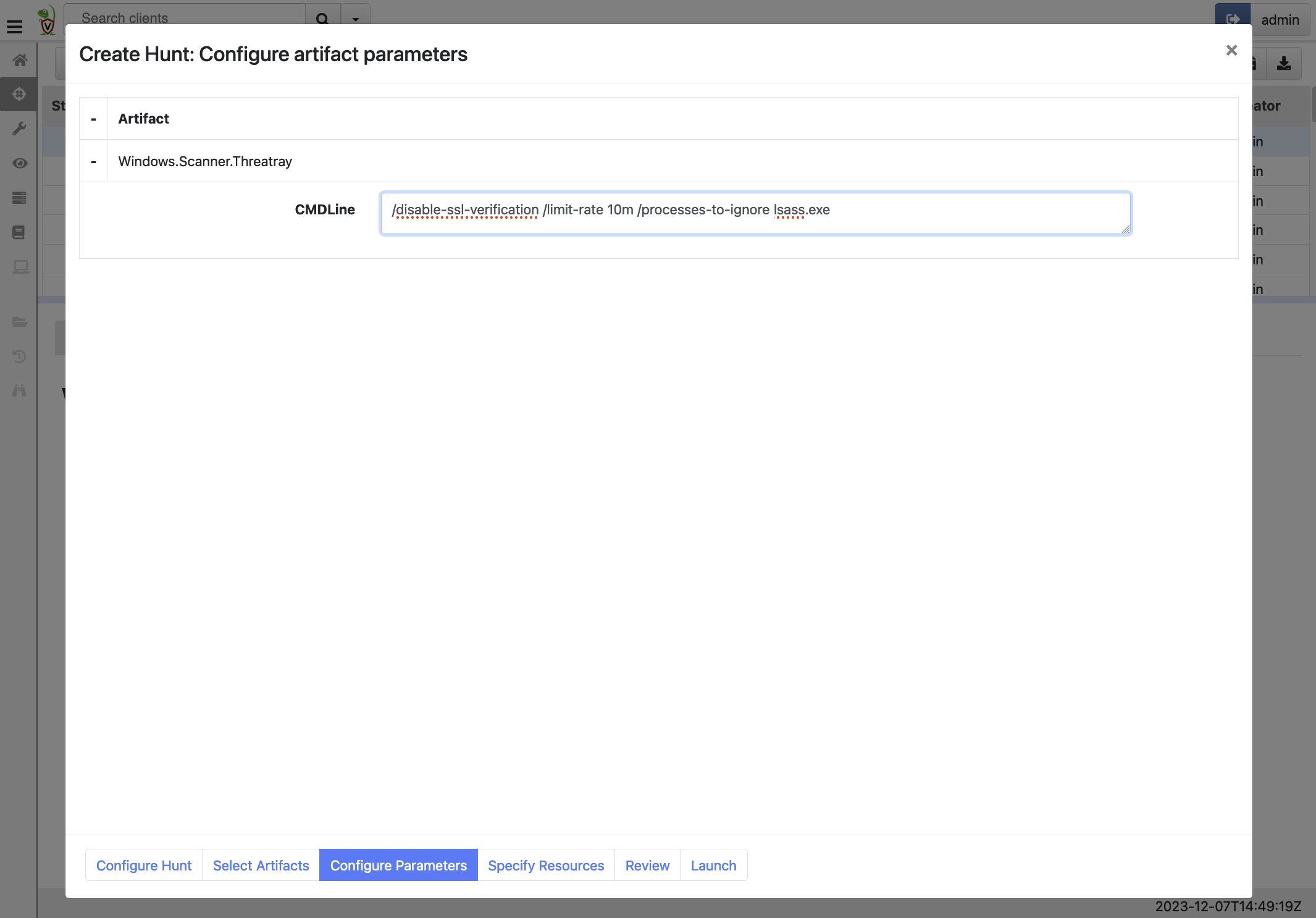
Configuration of optional command line parameters.
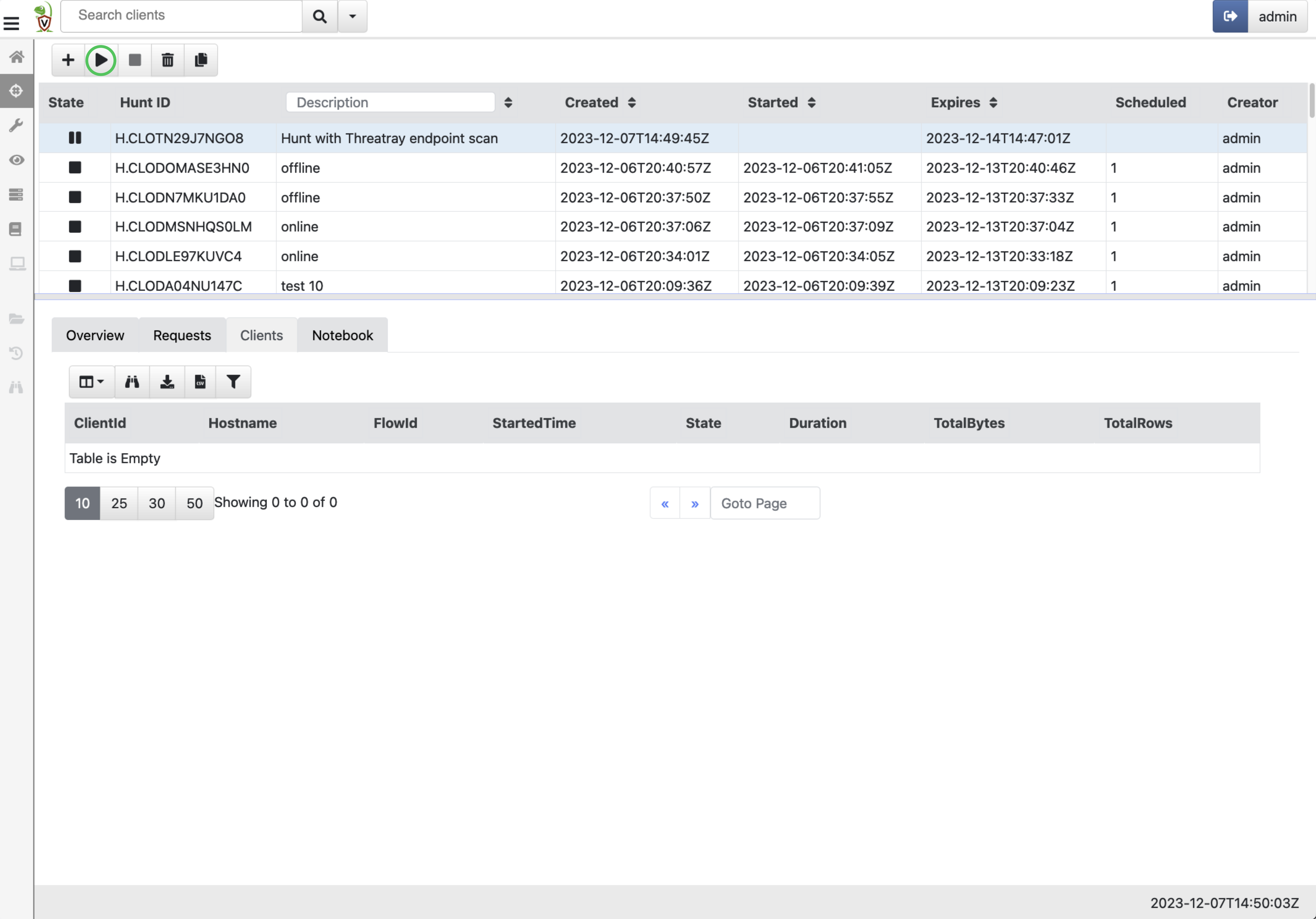
Starting the hunt.
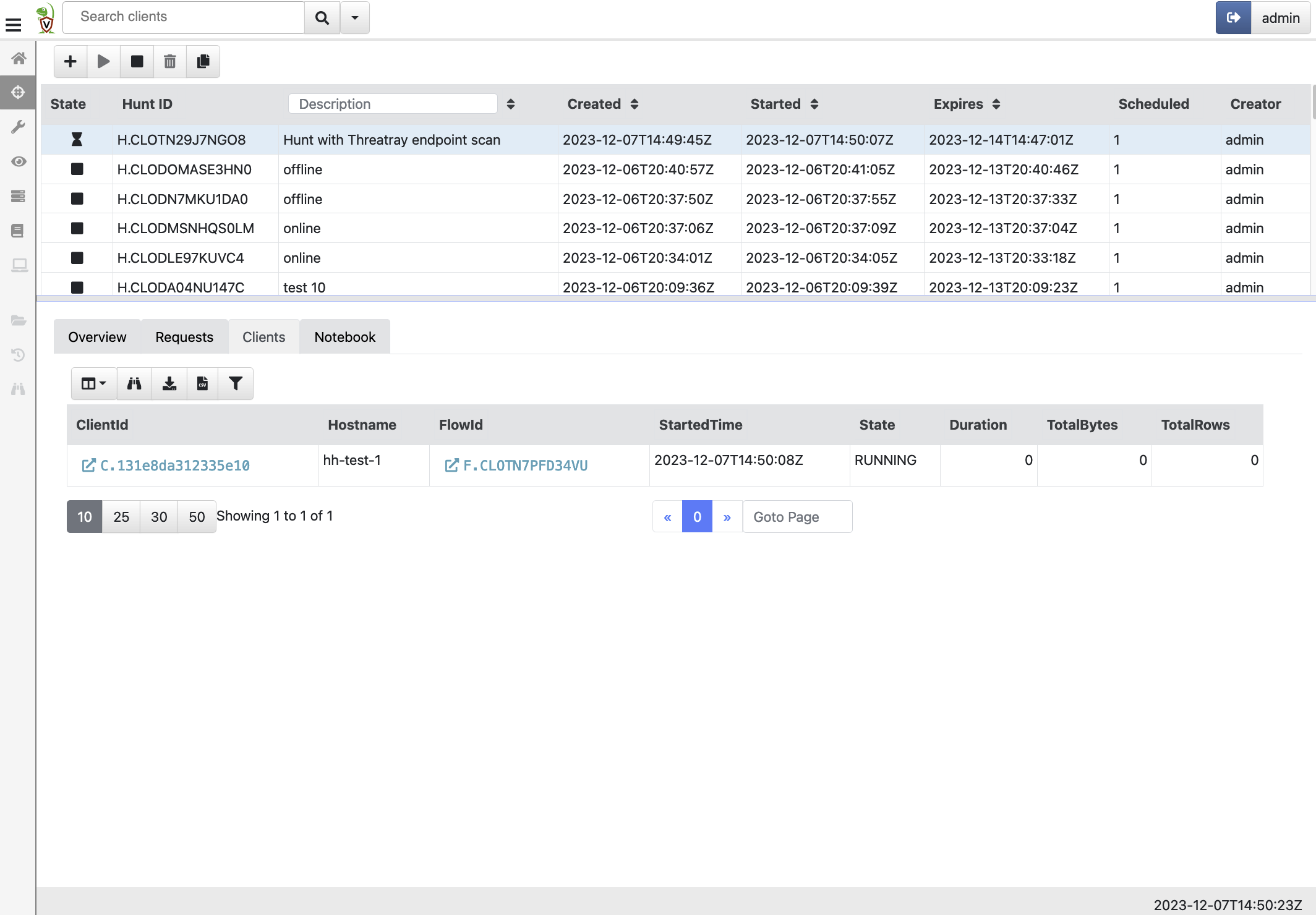
The hunt running on one host called hh-test-1.
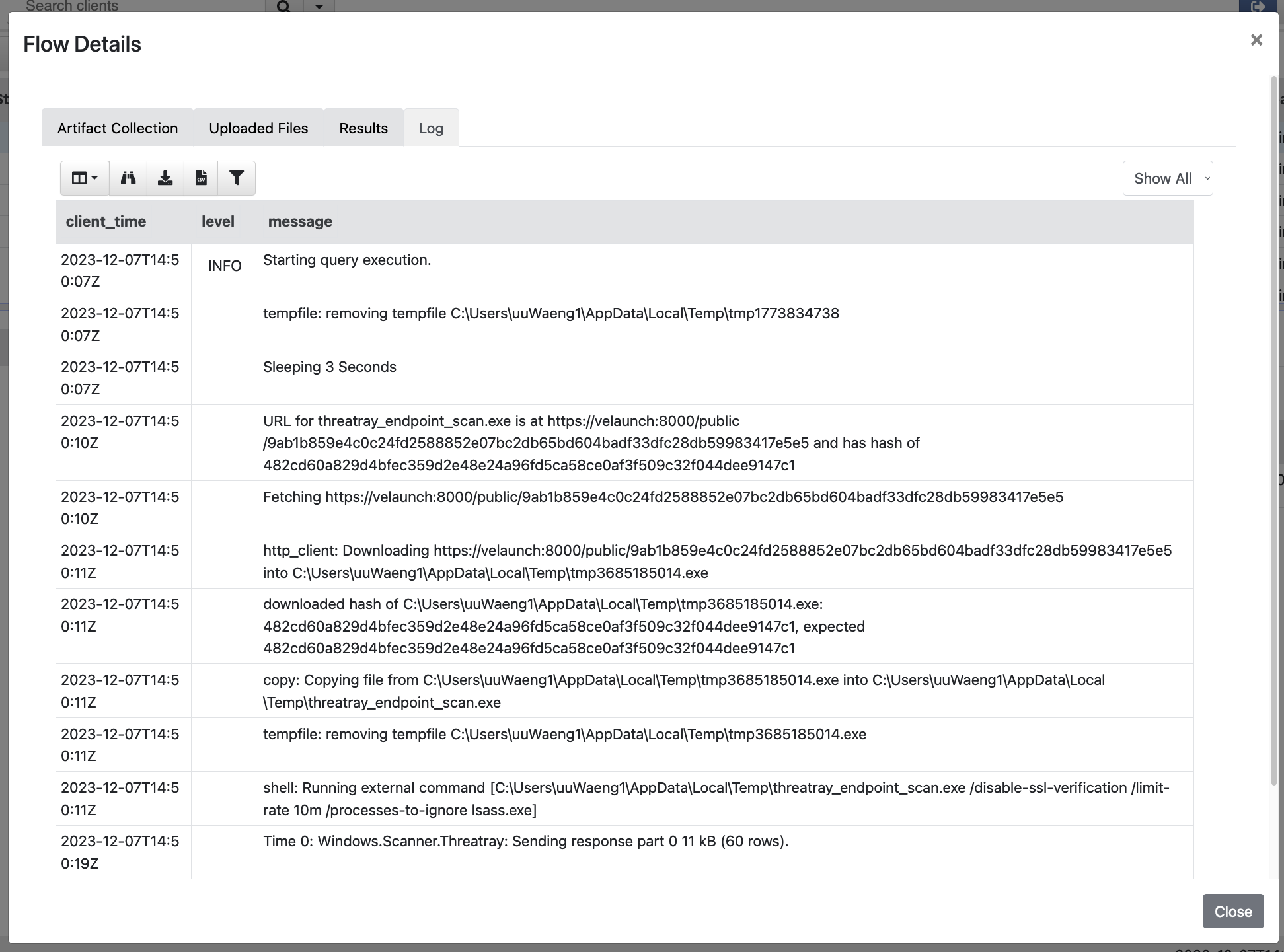
Flow logs of the hunt on the host hh-test-1.
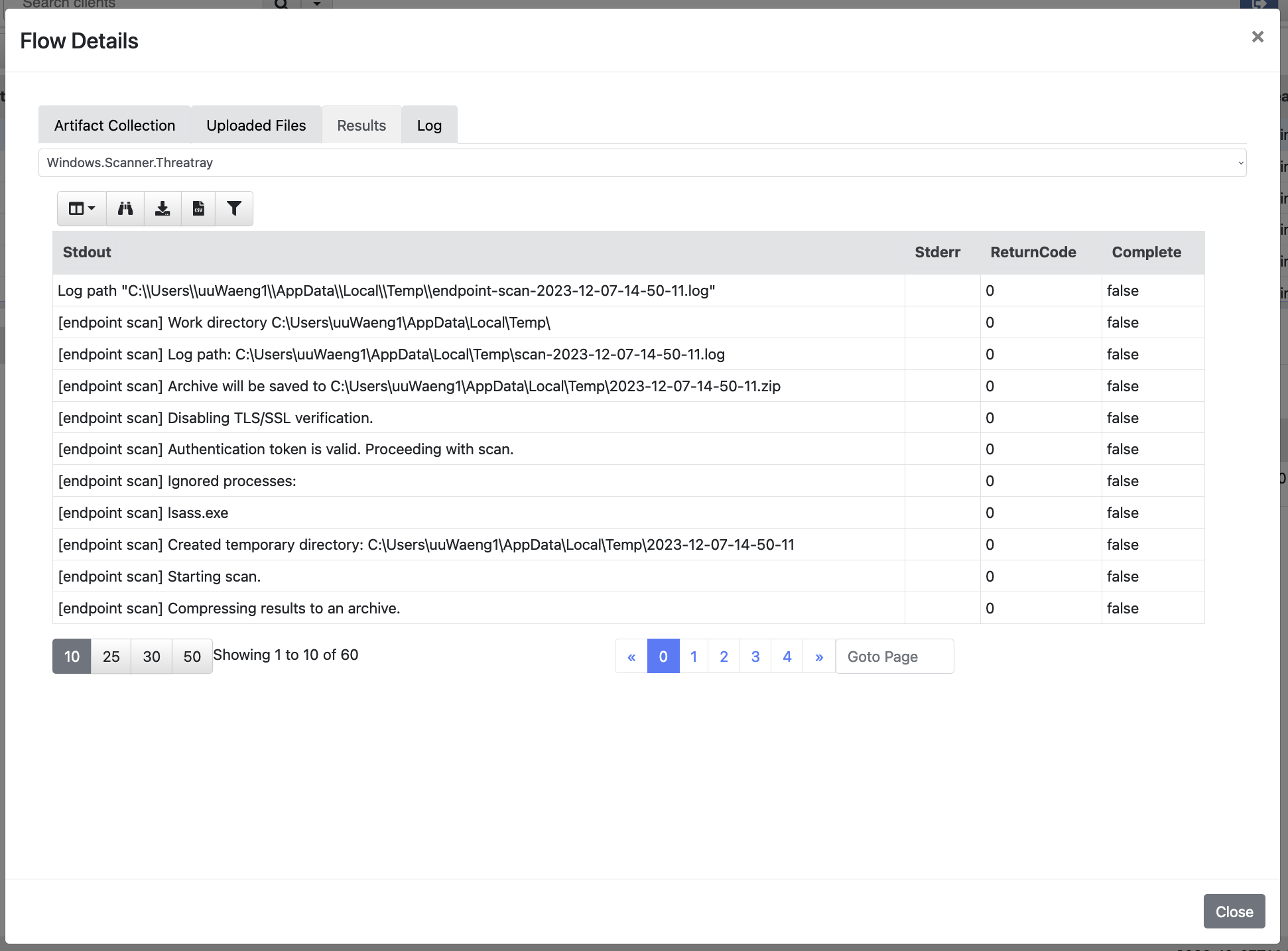
Threatray endpoint scan logs.
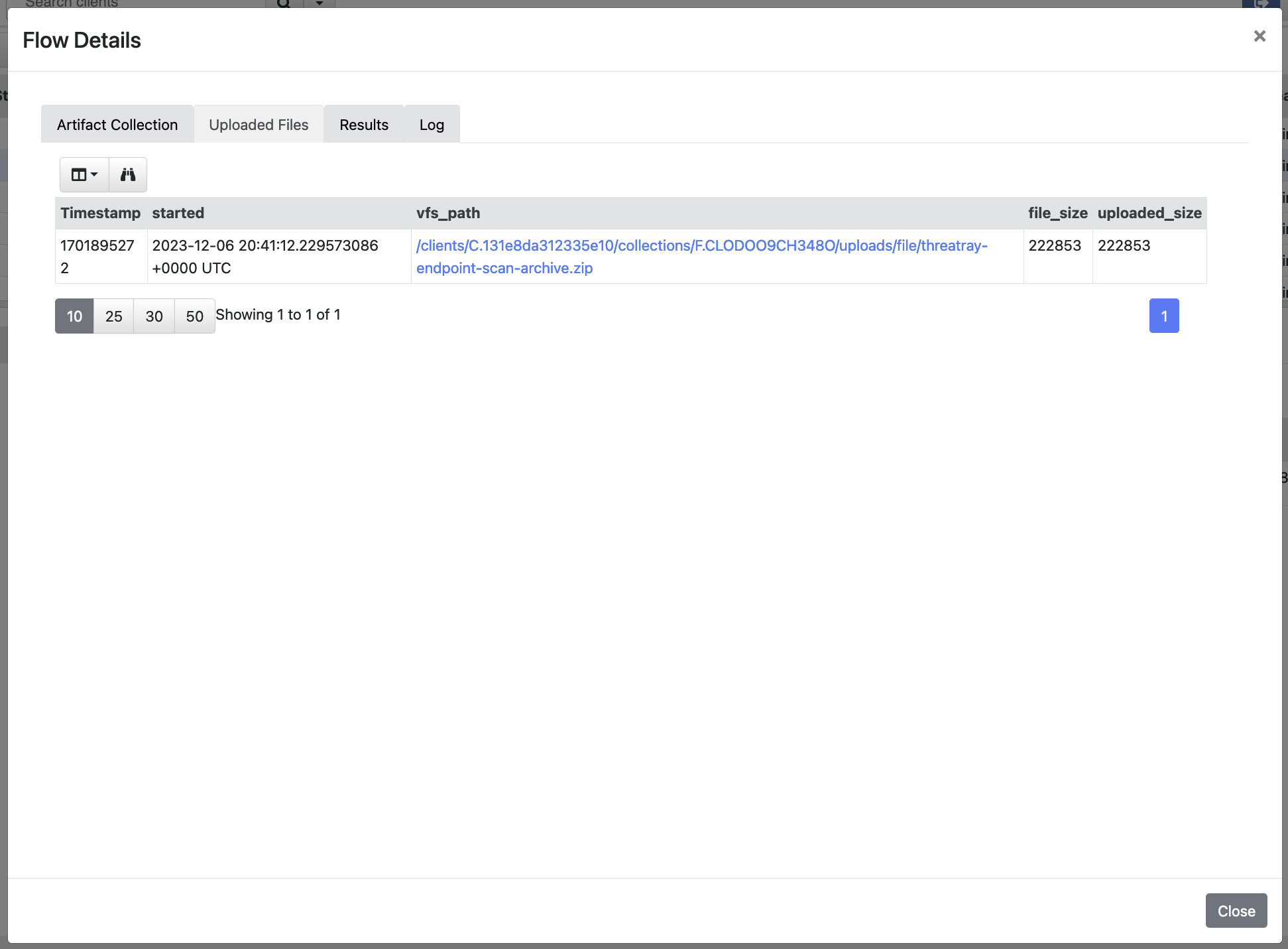
The uploaded archive, that can be submitted to Threatray, in case the Archive artifact was used.
After the hunt has finished, the analysis results will appear in your Threatray instance.
Updated about 1 year ago