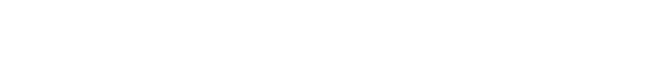
Submitting Files
Threatray supports the submission and analysis of multiple file types, URLs, and memory dumps, either through the user interface (UI) or the API.
All submissions remain private to your organization’s instance and are not shared with other users or with Threatray.
Dynamic and static file analysis
Dynamic analysis
Dynamic analysis executes a file within a sandbox environment. This method is recommended for all unknown files, unless specific circumstances require static-only analysis (see below). For documents and scripts, dynamic analysis is mandatory, as static analysis is not available for these file types.
The submission dialogue for dynamic analysis provides standard options such as selecting a virtual machine, setting the analysis duration, and configuring timeout settings. Advanced options are also available, including support for compound samples, DLL export calls, and optional command-line arguments.
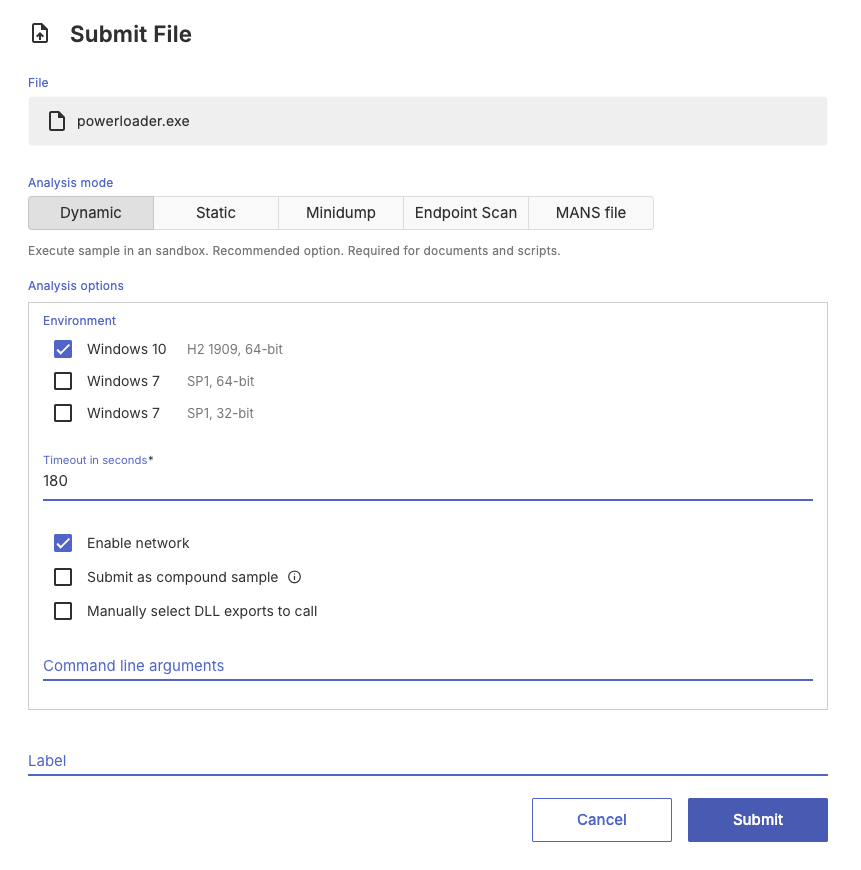
Static analysis
Static analysis is best suited for unpacked code, shellcode, code dumped from memory, manually unpacked code, broken PE files that cannot be executed.
In these cases, dynamic analysis is either unsuitable or unnecessary because the code cannot run or has already been unpacked. Advanced users can further refine static analysis by specifying parameters such as the base address of the code to be analyzed.
If Threatray does not automatically recognize your file during static analysis, you can bypass file type detection by renaming the file with the extension .bin. This forces the system to treat it as a Binary file.
⚠️ Note: Static analysis is not recommended for packed code. In such cases, use dynamic analysis to ensure proper unpacking and execution.
File types supported
Threatray supports the following binary file types (x86-32 and x86-64) for both dynamic and static analysis:
- Windows executable files (.exe, .dll, .sys, .ocx)
- Windows Installer files (.msi)
For static analysis, the following binary file types (x86-32 and x86-64) are supported:
- Shellcode and memory dumps of PE files (not executable but containing code)
For dynamic analysis, the following document and script file types are supported:
- PowerShell scripts (.ps1)
- Visual Basic scripts (.vbs, .vbe)
- Command and batch files (.cmd, .bat)
- Microsoft link files (.lnk)
- JavaScript files (.js, .jse)
- Microsoft documents (.docx, .xlsx, .pptx, etc.)
- PDF documents (.pdf)
- OneNote documents (.one)
- Others (.hta, .chm, .wsf)
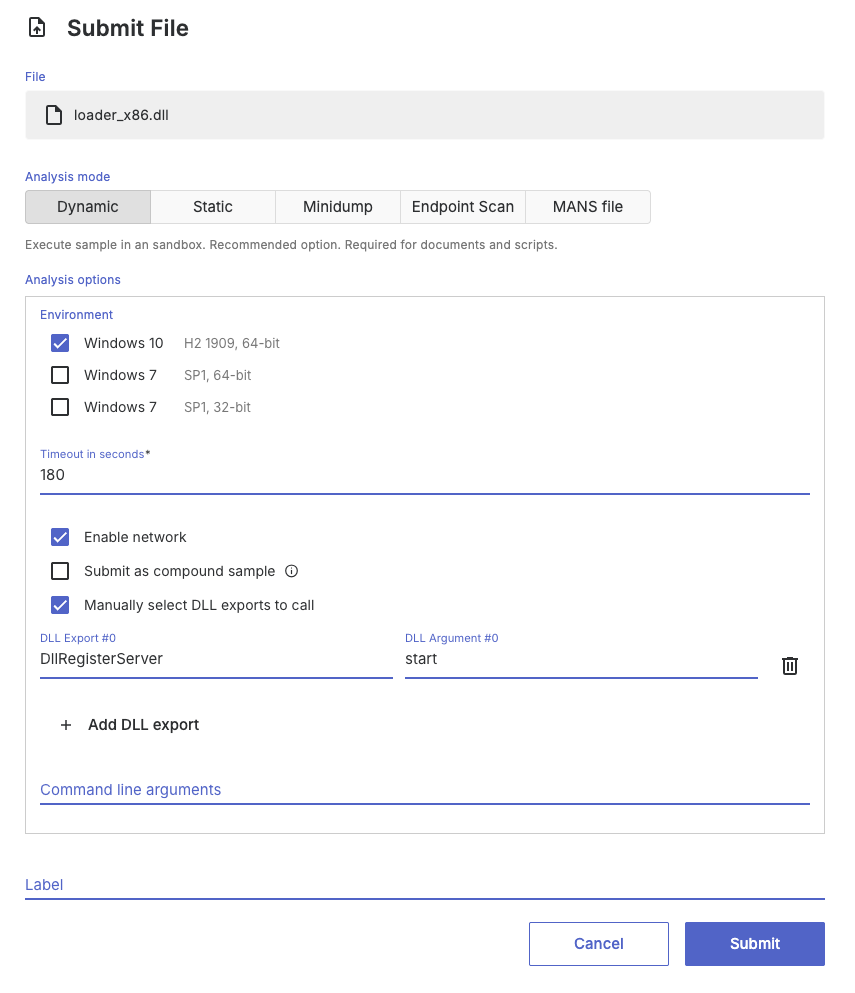
Submission of DLLs
When DLL files are submitted for dynamic analysis, Threatray automatically invokes all DLL exports during the sandboxing phase. If a DLL contains more than 20 exports, Threatray executes the first 10 and the last 10.
You can override this default behavior by explicitly selecting which DLL exports to invoke using the options in the submission dialog shown below.
Submission of archives
Threatray also supports archive submissions. By default, all files contained within an archive (up to 100) are analyzed individually. Submitting an archive is simply a faster alternative to uploading each file separately.
Supported archive formats include ZIP, 7-Zip, RAR, gzip, POSIX-tar, and ISO9660.
If needed, archives may be password-protected using the password infected.
Submission of compound files
Compound submissions typically consist of an EXE or DLL file executed during dynamic analysis, which requires additional supporting files in the analysis environment to run correctly. This is especially common in DLL sideloading scenarios, but also applies to other cases.
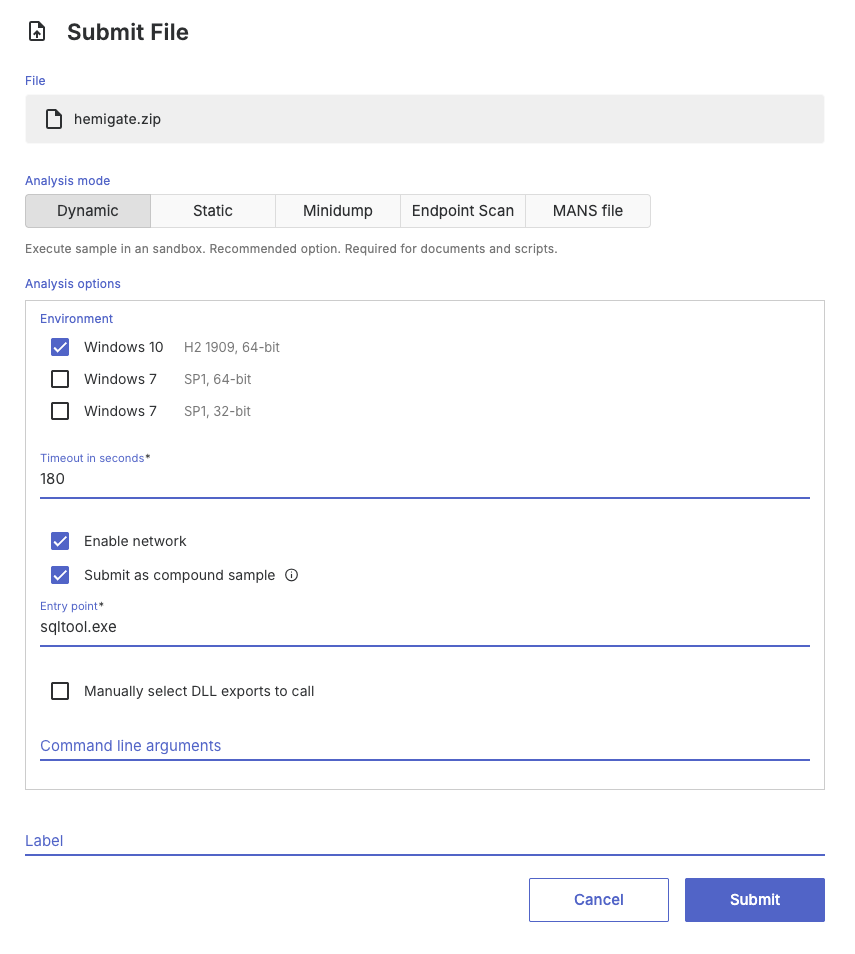
For example, consider a sample from the HemiGate malware family. In this case, the sqltool.exe file is the main executable, but it also depends on accompanying DLL, DAT, and DOC files:
sqltool.exe
K7AVWScn.dll
sqltool.dat
sqltool.doc
To submit this compound sample, add all four files to a ZIP archive, select the Submit as compound sample checkbox, and upload the archive to Threatray. In the submission dialog, designate sqltool.exe as the entry point for execution.
By default, the files are extracted to: C:\Users\%USERNAME%\Desktop\
This directory becomes the working directory for the entry point. If certain files within the archive, such as batch scripts or PowerShell scripts, need to access other files in the archive, you may need to use absolute paths. This is necessary because processes such as cmd.exe or powershell.exe may execute with a different working directory.
Compound submission can also be combined with features available in DLL analysis (e.g., specifying which export function to call) as well as providing command-line parameters.
Providing command line arguments
Providing command-line arguments is straightforward using the command line field in the submission dialog.
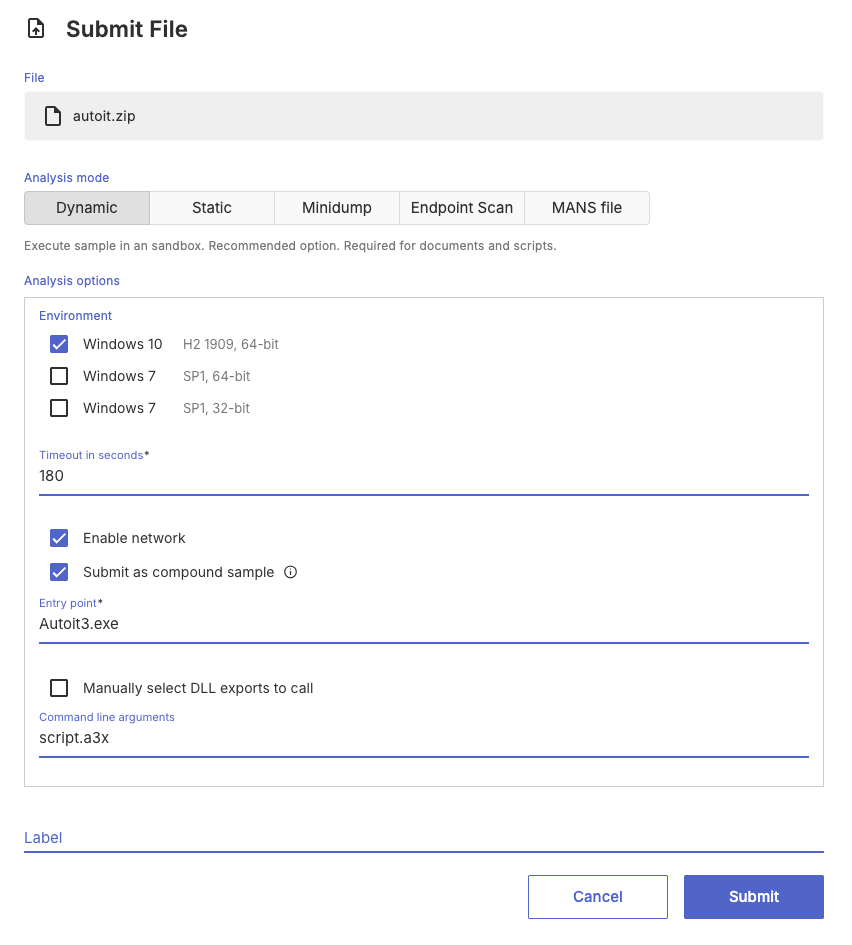
As an example, consider a compound sample from AutoIt that consists of the following files:
Autoit3.exe
script.a3x
We want to execute this as:
Autoit3.exe script.a3xTo achieve this, submit the files as a compound ZIP (see above), specify Autoit3.exe as the entry point, and set script.a3x as the command-line argument.
Minidump analysis
Minidump analysis provides a rapid means to investigate potential malware infections within a minidump of a process. To this end Threatray conducts static analysis on all memory sections within a minidump.
Various methods exist for generating minidumps; to create a minidump of the process on the targeted system, we recommend using Sysinternals’ procdump.exe with a user account having elevated privileges and the -ma flag:
procdump.exe -ma <pid>While minidumps from other tools are acceptable for submission, they might lack crucial memory fragments needed for effective threat identification.
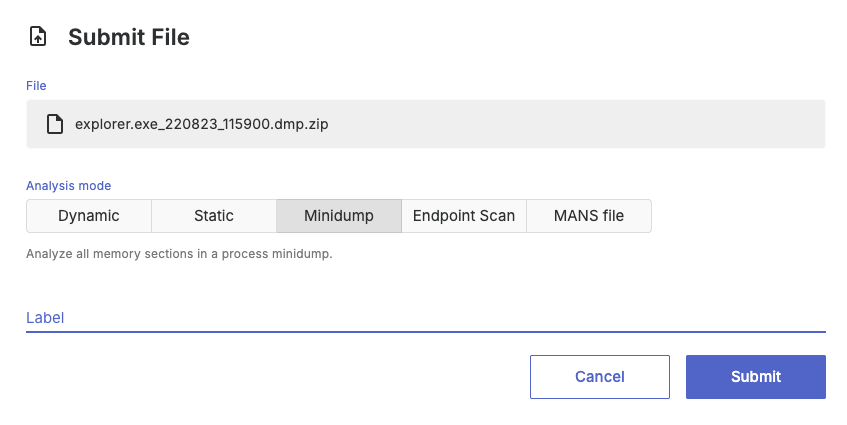
To upload a file for Minidump analysis, use the file submission UI and select the Minidump analysis mode.
Trellix HX MANS analysis
Trellix HX provides the capability to acquire process memory data from host endpoints with the process-memoryacquire audit, as detailed in this documentation. The acquisition generates a MANS file, which Threatray can analyze by performing static analysis on all memory sections within the file.
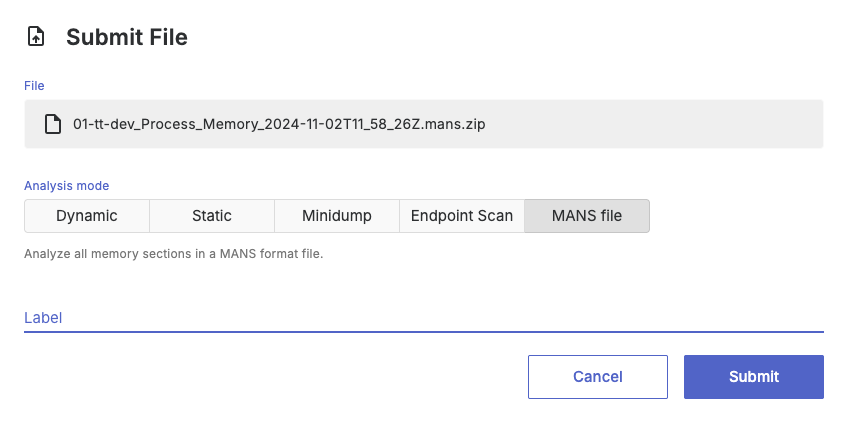
To upload a file for MANS analysis, use the file submission UI and select the MANS analysis mode.
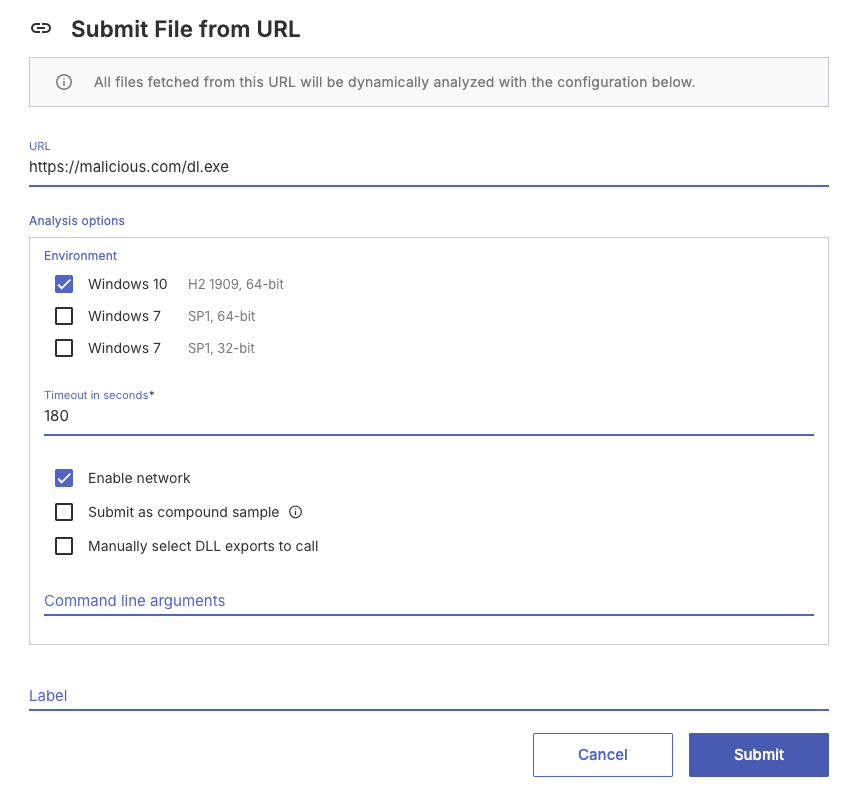
Analyzing files using URLs
As an alternative to file submission, you can provide a URL for analysis. The system loads the URL in a web browser, attempts to download the referenced file, and then performs dynamic analysis on it.
Updated 4 months ago