Searching
Threatray’s search allows users to explore both your private data and a global threat feed with a range of search options. Private data is all data that you and your team have uploaded to Threatray, while the threat feed contains a continuously growing repository of 100+ millions malware samples, covering cybercrime, ransomware, C2 frameworks, APTs, hacking tools and more.
Search queries
The following data is searchable:
- Metadata: Hashes, submission labels, malware family names, file names
- Behavior Artifacts from Dynamic Analyses: IP, Domain, URL, mutexes, registry entries, process names
- Retrohunt: Code-wise similar samples
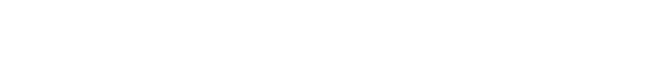
The search is available both in the UI and via the API. The UI has a help section on searching once you enter the search bar (1), including examples of searches (2).
You can specify the scope of your search (private, public/global, or both) via the dropdown next to the search bar (3).
The search engine operates on the following syntax [operator:] "search term"
- operator (optional): Specifies the field to search, like ‘hash’, ‘label’, ‘ip’, etc.
- search term: The term to search for. Use “quotes” if spaces or special characters are present.
Multiple search terms can be connected with spaces using AND logic. Wildcards (*) and single-replace (?) are supported.
Here are some examples of search queries:
label: "test-case-1"
1f421ed*
process: “*services.exe" ip:"40.113.200.201"
mutex: "Global\client_36672"
sample-name: "*ransom?are.exe"
retrohunt: 8d41d5131fac719cc11823fb57bef9ef1ea063dbb8f52b235a3948bece039d95The following search operators are available:
- ip: Contacting an IP or IP range (ex: 192.168.1.0/24)
- url: Contacting an URL
- domain: Contacting a domain
- file: Modifying a file (path)
- mutex: Modifying a mutex
- registry : Modifying a registry key
- process: Process name and command line
- signature: Malware family detection
- label: Label assigned to a file during submission
- sample-name: Submitted file name
- analysis-id: Analysis ID
- file-hash: Submitted file hash (MD5, SHA1, SHA256)
- memory-hash: Memory region hash (MD5, SHA1, SHA256)
- retrohunt: Retrohunt for similar samples, using the hash as selector
If an ‘operator:’ is omitted, the system attempts to deduce the type of search based on the input (e.g., ‘hash:’ for hashes, ‘ip:’ for IPs).
Search results
When you issue a search query, the search view will open and display the results.
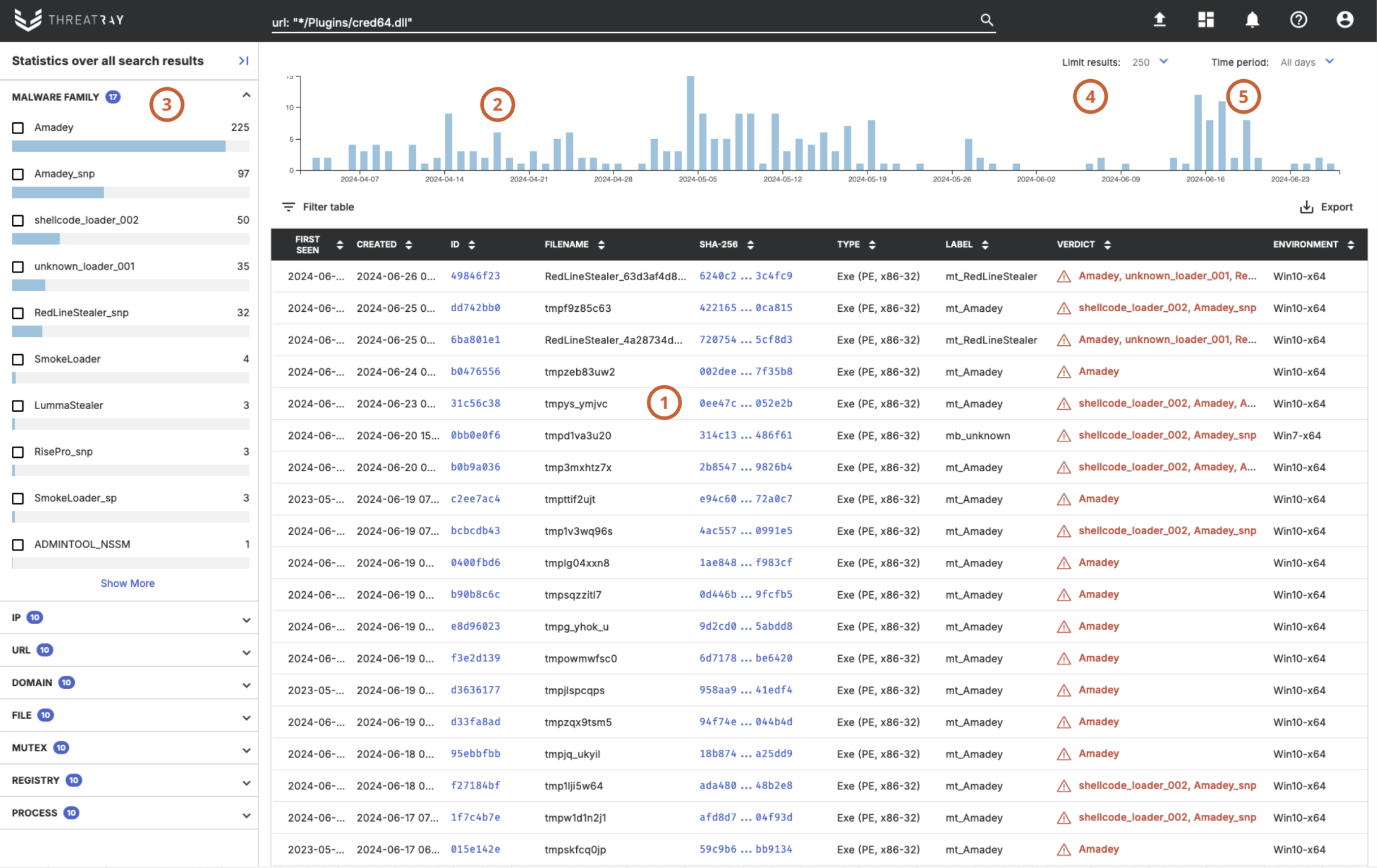
The list of matching sample analyses is displayed (1), ordered by the date the samples were first seen. For Retrohunts, the list is ordered by similarity score, with more details available here. There may be multiple analyses for the same sample. Each analysis can be opened by clicking its ID. The timeline above (2) shows the distribution of samples from the matching analyses based on their first seen timestamps. The left-hand side displays statistics (3) gathered from the matching analyses, including the malware family and behavioral artifacts, as described here. Clicking on any entry in the statistics will refine the search query by that term, allowing for more precise results.
The number of search results is limited to 250 entries; it can be adjusted with a dropdown menu (4). The search time period is unlimited by default; it can be changed to include only the last 7-90 days (5).
Updated about 18 hours ago